Insufficient Hardening – Password Set to Not Expire
TCM-KB-INT-004
Last Updated: 8/17/2023
Windows Operating Systems
The recommended remediation steps and configurations described in this response would primarily affect systems running Microsoft Active Directory (AD) as a part of their IT infrastructure.
SMB
SMB refers to Server Message Block.
A small message block refers to a compact unit of data transmission used in communication protocols. It typically contains a limited amount of information, such as a command, status update, or a small portion of a larger message, allowing for efficient and rapid exchange of data between devices or systems.
Contributor

Joe Helle
Chief Hacking Officer
This Knowledge Base Article was submitted by: Joe Helle.
Recent Blogs

AI Assisted Pentest Reporting
In this blog, we’ll show how to generate pentest finding templates with DeepSeek AI using MITRE’s Common Weakness Enumeration (CWE) categories.
Security Misconfiguration
Issue
Accounts in the domain have passwords that do not expire.
Recommended Remediation
The following outlines the recommended steps that the systems and network administrators should take in order to secure the environment. Note that any time a modification such as this is made, it is vital that the organization first take time to audit the necessity of each account with the PasswordNeverExpires attribute set to true (as is common with some service accounts, KRBTGT account, etc.).
From a Windows device with the Active Directory module installed, identify accounts with passwords that don’t expire using the following command:
get-aduser -filter * -properties Name, PasswordNeverExpires | where { $_.passwordNeverExpires -eq “true” } | where {$_.enabled -eq “true”}
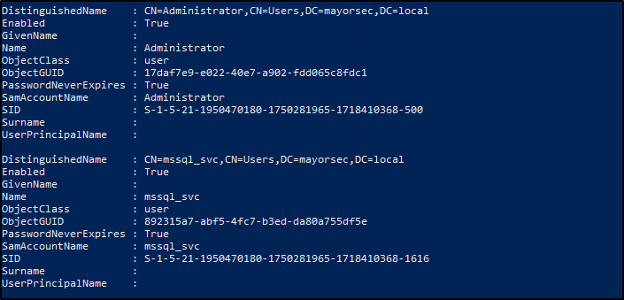
Different options exist to modify the PasswordNeverExpires value to false.
PowerShell Remediation
After auditing the vulnerable accounts, determine if a full remediation is appropriate, or if singular remediation is appropriate.
If all accounts should be remediated, the following PowerShell command can be executed:
Get-ADUser -Filter {(ObjectClass -eq “user”)} | Set-ADUser -PasswordNeverExpires:$FALSE
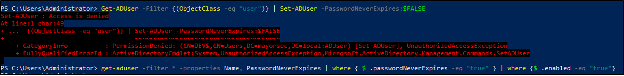
Note that an access denied error here is expected.
If singular accounts should be remediated, the following command can be executed per user account:
Set-ADUser -Identity mssql_svc -PasswordNeverExpires:$FALSE
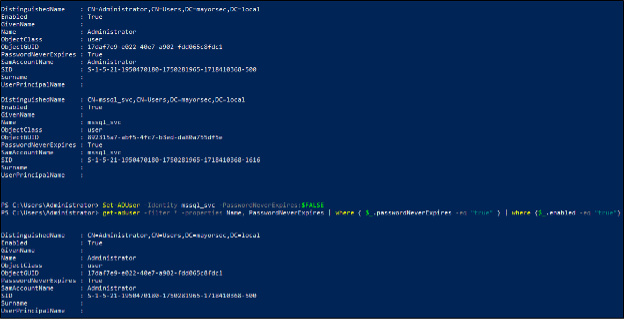
Note that the mssql_svc user account is no longer listed as having a password that never expires.
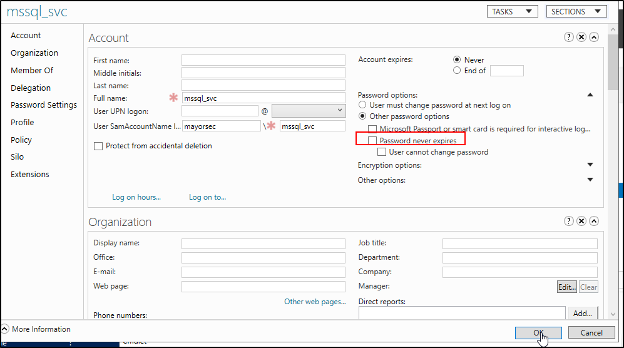
Active Directory Administrative Center Remediation
From the Active Directory Administrative Center, open the username in question (i.e., mssql_svc) and note that the “Password never expires” checkbox is checked.
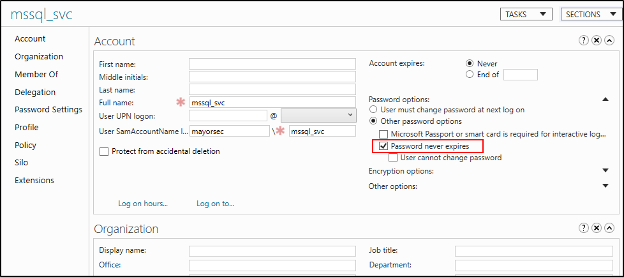
To remediate, uncheck this box and press OK at the bottom of the window. Use the previously run PowerShell commands to confirm successful remediation. Note the absence of the account when remediated.

See What We Can Do For You
Download a sample penetration test report to see the results we can deliver for your organization.
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.
