Security Misconfiguration
Users and Computers Can Create and Delegate Computer Accounts
TCM-KB-INT-001
Last Updated: 6/14/2023
Microsoft Windows Server
The recommended remediation steps and configurations described in this response would primarily affect systems running Microsoft Active Directory (AD) as a part of their IT infrastructure.
Active Directory
Active Directory is a directory service developed by Microsoft for Windows domain networks, and it provides centralized management and authentication services for the network.
Contributor

Joe Helle
Chief Hacking Officer
This Knowledge Base Article was submitted by: Joe Helle.
Recent Blogs

AI-Automated Credential Stuffing
Credential stuffing remains one of the most efficient paths to account takeover, and AI assistance is changing the scale and effectiveness of those attacks.

OSINT Resources and Tools
Explore some of the fundamental domains of OSINT research, plus a list of tools and resources to develop this discipline as a cyber security professional.

Networking Fundamentals for Pentesters
We will take a look at networking concepts you should focus on, why they matter, and resources for learning for beginning pentesters without an IT background.

The PSAA: SOC Experience Certification
The PSAA certification is designed to give you knowledge and hands-on SOC experience, while signaling to employers that you can contribute on day one.

How To Get Into Cyber Security With No Experience
Breaking into cybersecurity with “no experience” is really about learning, creating your own experience, and networking. Here are some strategies that can help.
Security Misconfiguration
Issue
Default Active Directory deployments permit valid domain user and computer accounts to create up to ten (10) computer accounts in the domain. This default is configured in the MS-DS-Machine-Account-Quota attribute in the domain.
Recommended Remediation
The following outlines the recommended steps that the systems and network administrators should take in order to secure the environment.
Administrators can determine the attribute value via ADSI. To view the Attribute via ADSI and modify it, use the following steps:
-
- Open the Server Manager with a privileged account, click the Tools menu, and select ADSI Edit
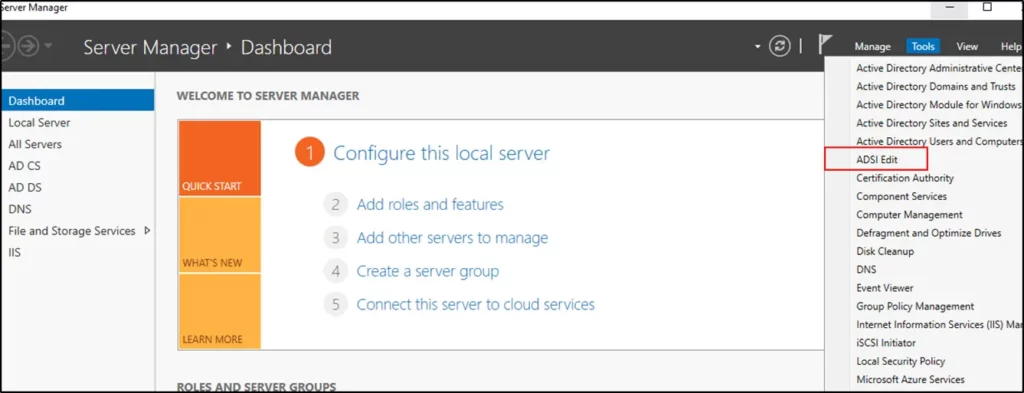
- Open the Server Manager with a privileged account, click the Tools menu, and select ADSI Edit
-
- In the ADSI Edit window, select Action, Connect To, and enter the appropriate information for the domain. In most cases, the default settings are valid for this task. Click OK once verified.
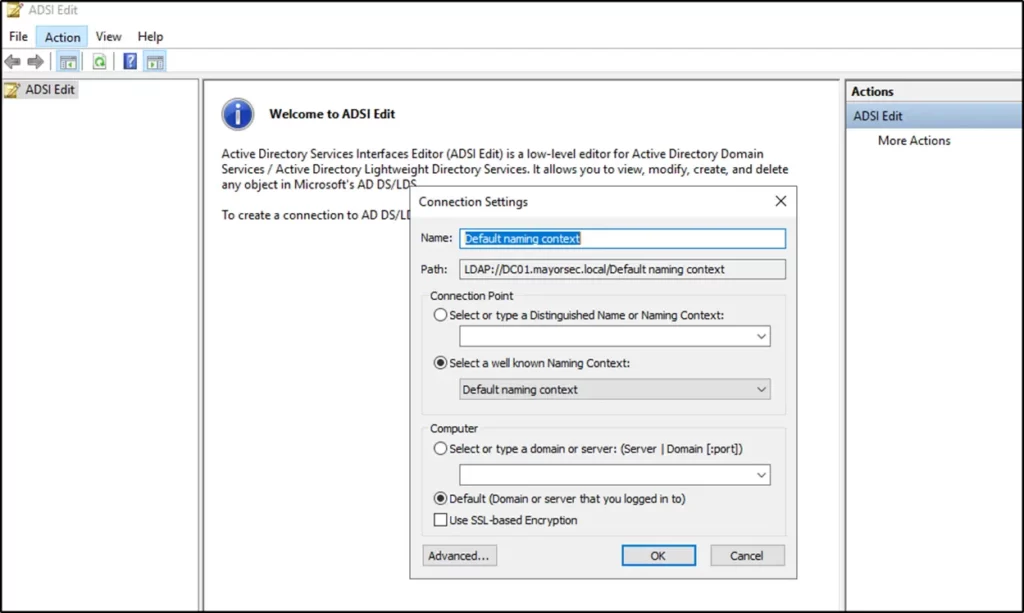
- In the ADSI Edit window, select Action, Connect To, and enter the appropriate information for the domain. In most cases, the default settings are valid for this task. Click OK once verified.
-
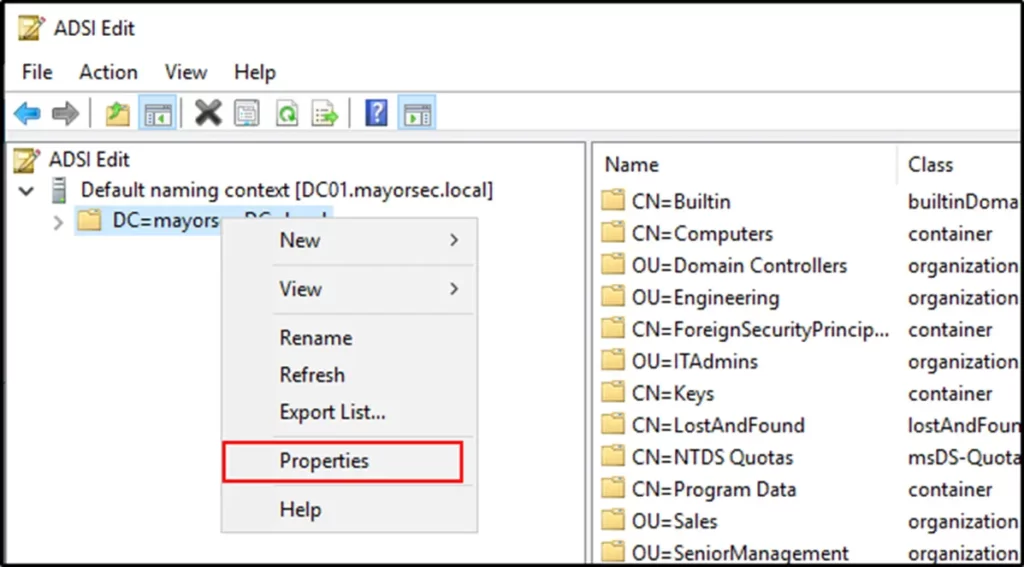
- Click the drop down for the new naming context, right click the directory beginning with DC=, and select Properties
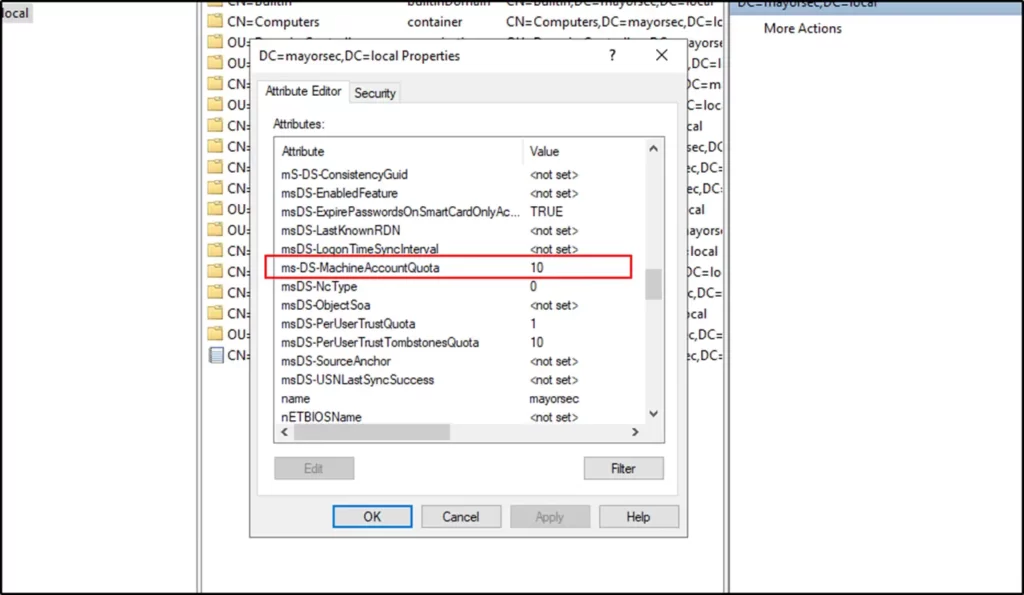
- In the Properties window, scroll down to ms-DS-MachineAccountQuota, and observe the value. Reduce the value to zero, or whichever value your organization has deemed appropriate.
- Utilizing a non-domain joined computer for testing, attempt to join the computer to the Active Directory environment. When configured correctly, an error should occur stating that the computer cannot join the domain.
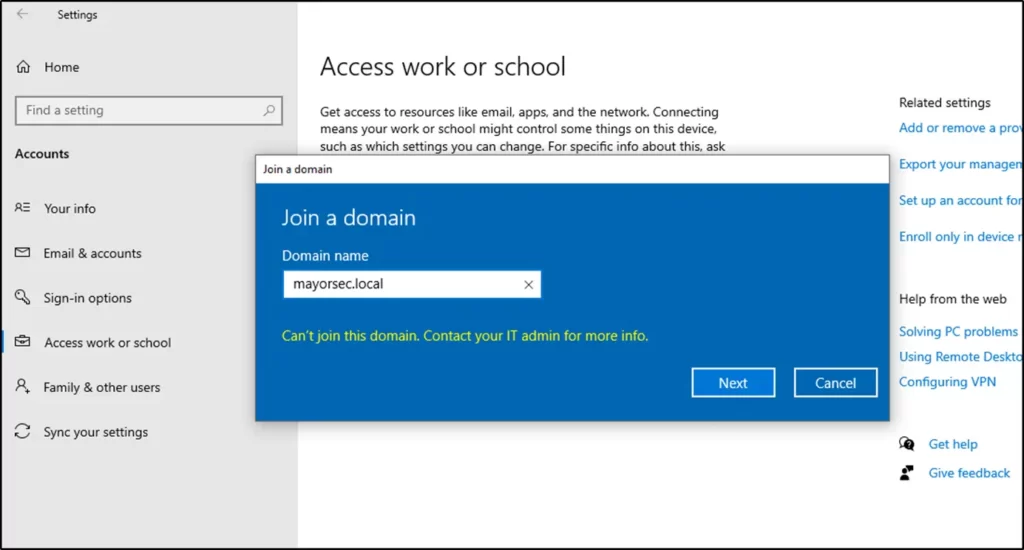
- In the Properties window, scroll down to ms-DS-MachineAccountQuota, and observe the value. Reduce the value to zero, or whichever value your organization has deemed appropriate.
- Click the drop down for the new naming context, right click the directory beginning with DC=, and select Properties
The process can also be replicated utilizing PowerShell. Utilize the following command to query the ms-DS-MachineAccountQuota value:
-
- Get-ADObject -Identity ((Get-ADDomain).distinguishedname) -Properties ms-ds-machineaccountquota
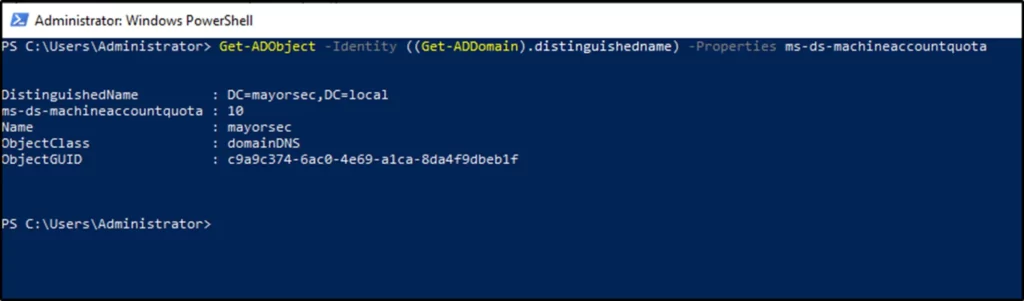
- Get-ADObject -Identity ((Get-ADDomain).distinguishedname) -Properties ms-ds-machineaccountquota
Utilize the following PowerShell command to set the value to zero (0), and check the value afterwards. Ensure that the domain name reflects the current domain
-
- Set-ADDomain -Identity <domain> -Replace @{“ms-ds-machineaccountquota”=”0”}
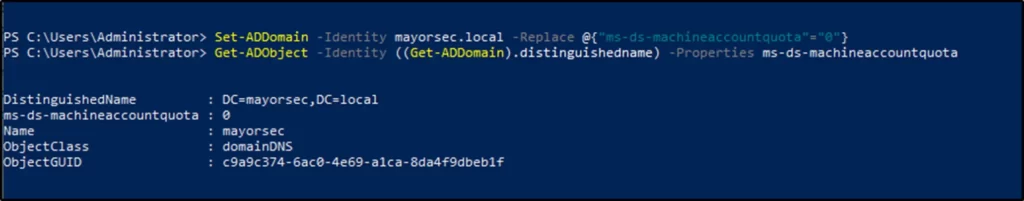
- Set-ADDomain -Identity <domain> -Replace @{“ms-ds-machineaccountquota”=”0”}

See What We Can Do For You
Download a sample penetration test report to see the results we can deliver for your organization.
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.
