Insufficient Hardening – SMB Signing Not Required in Windows
TCM-KB-INT-003
Last Updated: 6/30/2023
Microsoft Windows Server
The recommended remediation steps and configurations described in this response would primarily affect systems running Microsoft Active Directory (AD) as a part of their IT infrastructure.
SMB
SMB refers to Server Message Block.
A small message block refers to a compact unit of data transmission used in communication protocols. It typically contains a limited amount of information, such as a command, status update, or a small portion of a larger message, allowing for efficient and rapid exchange of data between devices or systems.
Contributor

Joe Helle
Chief Hacking Officer
This Knowledge Base Article was submitted by: Joe Helle.
Recent Blogs
Security Misconfiguration
Issue
SMB signing is either not enabled or is enabled but not required, which could result in additional compromise, such as the dumping of hashes, relaying of credentials, or takeover of endpoints.

Recommended Remediation
The following outlines the recommended steps that the systems and network administrators should take in order to secure the environment. This section will be broken up into two categories – individual Windows endpoints, and via GPO in Active Directory.
Enable and Require Signing on an Individual Windows Machine
- Utilizing an account with administrative privileges, open the Local Group Policy Editor. Under Computer Configuration, select Windows Settings -> Security Settings -> Local Policies -> Security Options.
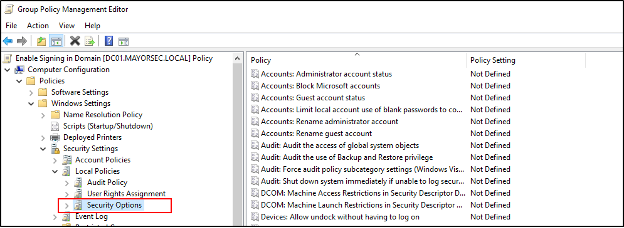
- Modify the following four Policy values, setting the Security Setting in each to Enabled. Ensure that you click Apply on each.
- Microsoft network client: Digitally sign communications (always)
- Microsoft network client: Digitally sign communications (if server agrees)
- Microsoft network server: Digitally sign communications (always)
- Microsoft network server: Digitally sign communications (if client agrees)


- Confirm that the change was made using a tool such as nmap.

Enable and Require Signing via GPO in Active Directory
- Utilizing an account with administrative privileges, access the Group Policy Management tool. Right click the domain the GPO will affect, and select Create a GPO in this domain, and Link it here. In the window that opens, name the new GPO (i.e., Enable Signing in Domain). Press ok when finished.


- Right click the new GPO, and click edit.

- Under Computer Configuration in the Group Policy Management Editor, select Windows Settings -> Security Settings -> Local Policies -> Security Options.

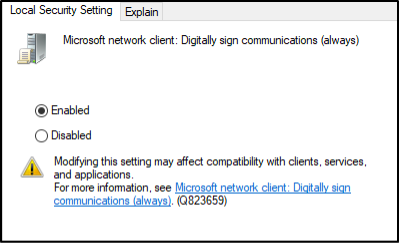
- Modify the following four Policy values, setting the Security Setting in each to Enabled. Ensure that you click Apply on each.
- Microsoft network client: Digitally sign communications (always)
- Microsoft network client: Digitally sign communications (if server agrees)
- Microsoft network server: Digitally sign communications (always)
- Microsoft network server: Digitally sign communications (if client agrees)


- By default, the domain controller will push the GPO update every 90 minutes. Alternatively, gpupdate /force can be used to push the modifications automatically.

- Confirm that the change was successful against the endpoints in the domain that were affected. The below shows the view from an attacker’s perspective when signing is enabled and required.


See What We Can Do For You
Download a sample penetration test report to see the results we can deliver for your organization.
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

