Insufficient Hardening – Users Can Run Command Prompt and PowerShell Terminals
TCM-KB-INT-005
Last Updated: 8/24/2023
Windows Operating Systems
The recommended remediation steps and configurations described in this response would primarily affect systems running Microsoft Active Directory (AD) as a part of their IT infrastructure.
Insufficient hardening
Insufficient hardening in cybersecurity is the failure to adequately secure systems against threats. This can result from using default passwords, running unneeded services, neglecting security patches, leaving network ports open, and lacking proper monitoring or logging. This leaves the system more susceptible to attacks.
Contributor

Joe Helle
Chief Hacking Officer
This Knowledge Base Article was submitted by: Joe Helle.
Recent Blogs

AI Assisted Pentest Reporting
In this blog, we’ll show how to generate pentest finding templates with DeepSeek AI using MITRE’s Common Weakness Enumeration (CWE) categories.
Security Misconfiguration
Issue
The organization allows users to open and execute commands from the Windows command prompt and PowerShell, or the organization already restricts through policy, but the policy is misconfigured.
Recommended Remediation
The following outlines the recommended steps that the systems and network administrators should take in order to secure the environment.
- Determine if end-users need access to Command Prompt and PowerShell terminal for day-to-day business functionality.
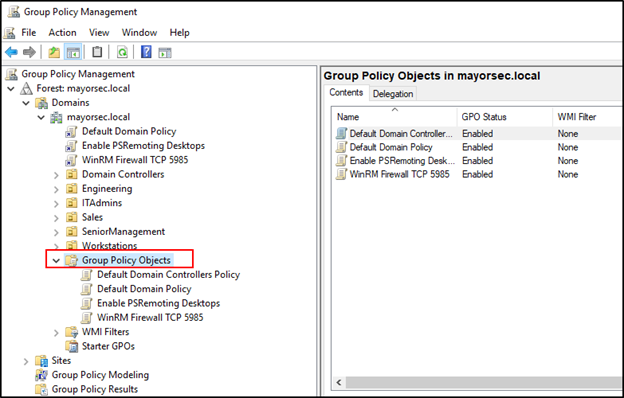
- Open the Group Policy Management Editor on the primary Domain Controller.
- In the editor, expand the Forest/Domain to edit, expand the individual domain, and expand Group Policy Objects.
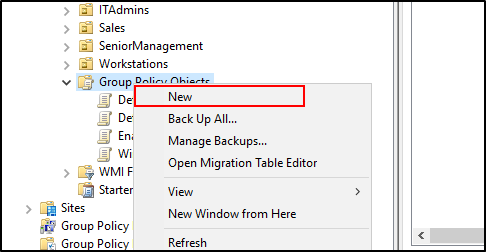
- Right-click Group Policy Objects and select New.
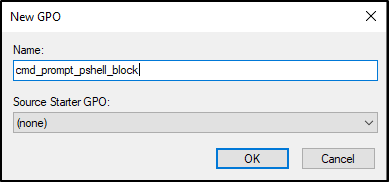
- Name the new GPO and press OK.
- Right-click the new GPO and select Edit.
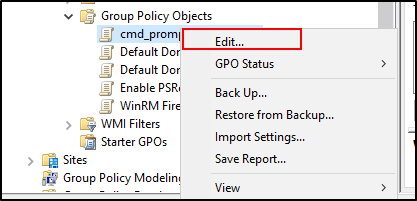
- Inside the new GPO window, expand User Configuration -> Administrative Templates -> System.
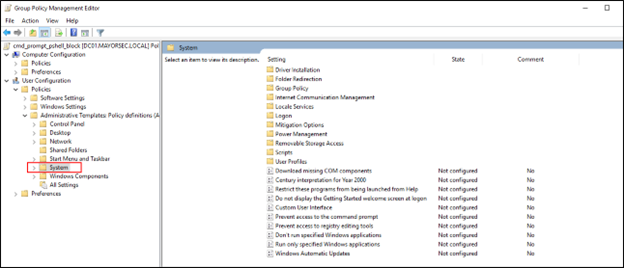
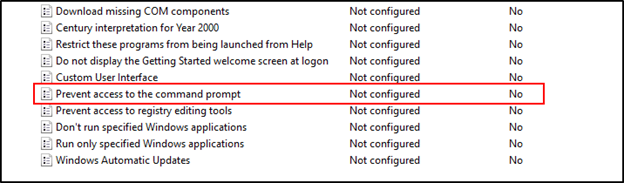
- In the window, two values exist that will be modified. First, double-click the “Prevent access to the command prompt” value to open it.
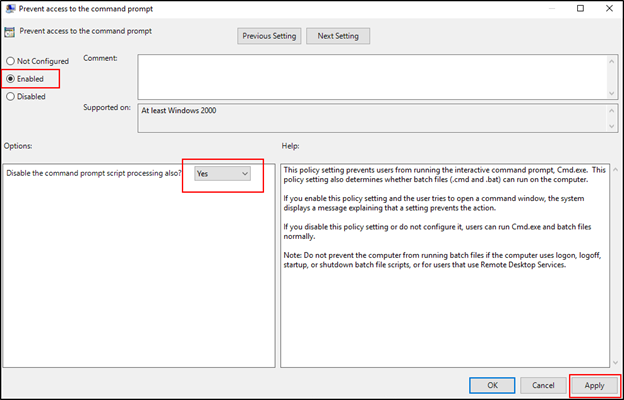
- In this window, set the value in the top left to “Enabled.” Under Options below, set “Disable the command prompt script processing also” to Yes. Press Apply and close the window. This will prevent the use of the command prompt, and script execution in Batch files.
- Next, double click the “Don’t run specified Windows applications” value to open the editor.
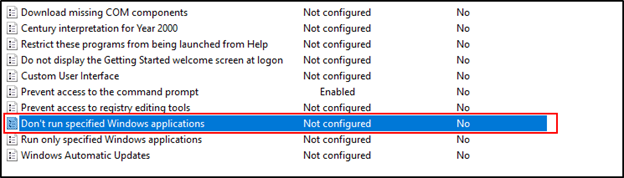
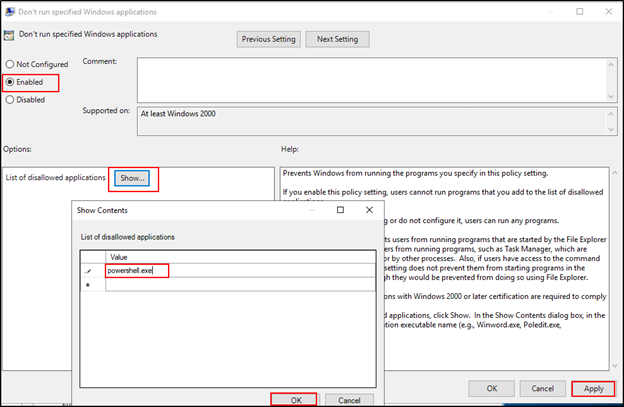
- In the editor, set the value in the top left to Enabled. Under Options, click Show next to “List of disallowed applications.” In the new window, enter “powershell.exe” into the first line. Press OK, which closes the window. Press Apply, and close the window.
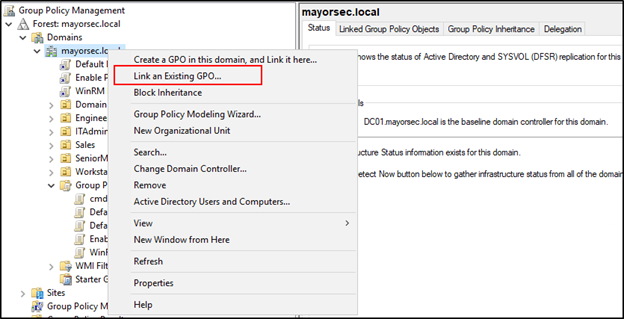
- The GPO needs to be linked to a domain. In the Group Policy Management window, right click the domain, and select “Link and Existing GPO.”
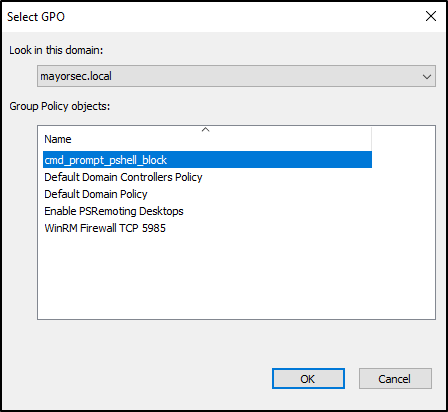
- In the new window, select the new GPO created and press OK.
- In the Group Policy Management window, click the new GPO, and select the “Delegation” tab to show the current users affected.
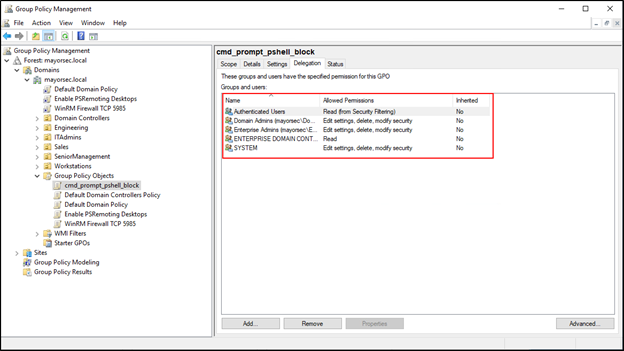
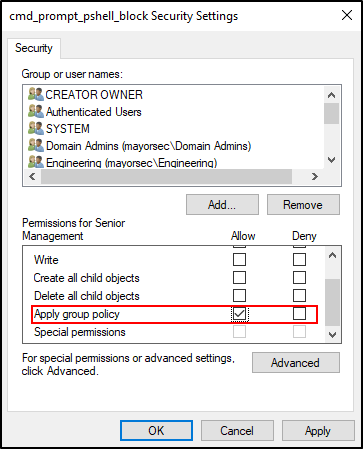
- By default, the GPO will be assigned to all Authenticated Users in the domain. This will restrict all users, including Domain and Enterprise Admin accounts, which is likely undesirable. Select the Advanced button at the bottom of the window to open the group editor.
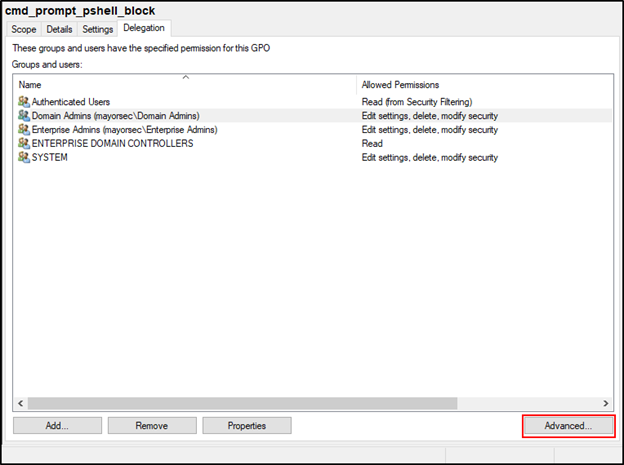
- Select Authenticated Users, scroll down under “Permissions for Authenticated Users,” and deselect “Apply group policy.”
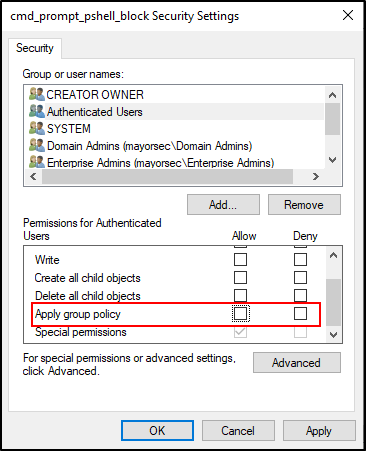
- Click the Add button to open the Select Users, Computers, Service Accounts, or Groups window. Click the Advanced Button in the new window.
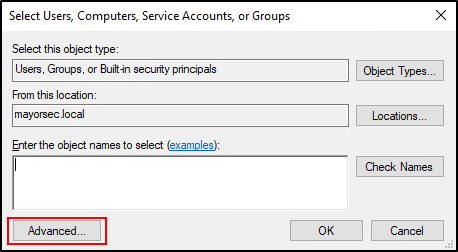
- Inside the window, click the “Find Now” button on the right side, which will provide a list of search results in the bottom. Multiple selections can be made in this list by using CTRL when clicking on each name. Once all selections are made, press OK.
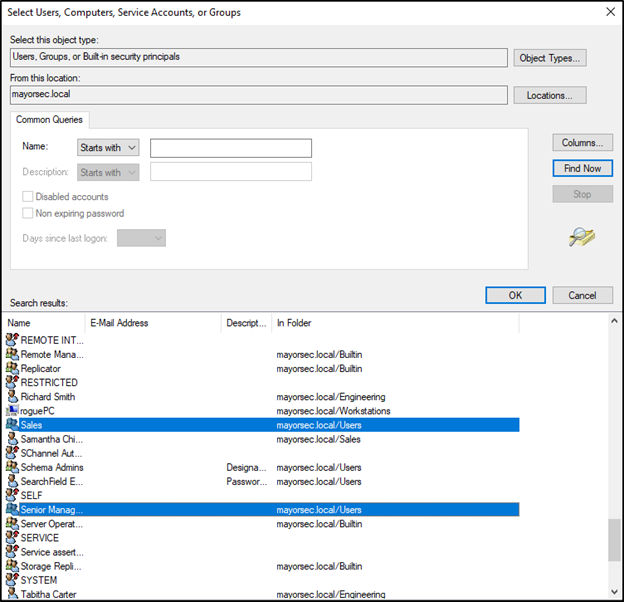
- The Select Users, Computers, Service Accounts, or Groups window should now have values in the object names box. Select OK to close this window.
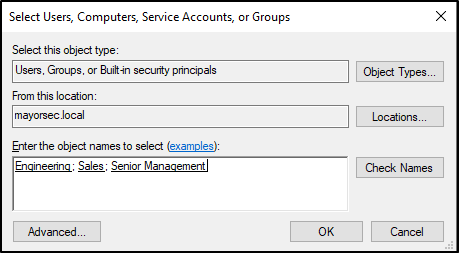
In the permissions window, select each group to apply the GPO to, and select “Apply group policy.” Once all selections have been made, select Apply, then OK to close the window.
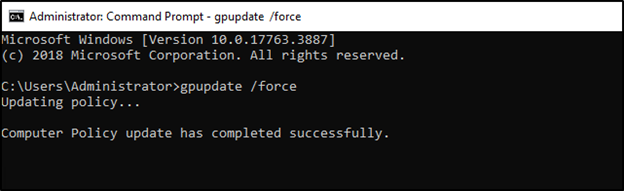
- Domain GPOs are updated every 90 to 120 minutes. To push the update sooner, open the command prompt on the domain controller, and enter “gpupdate /force.” Press enter to push the update.
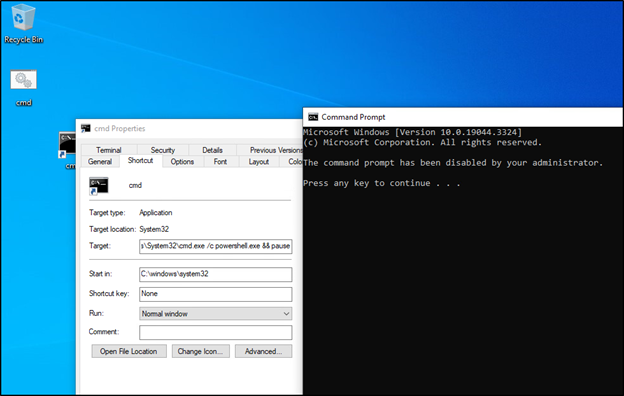
- Confirm the changes have been made by restarting a workstation on the domain, and logging in as a domain user affected by the GPO. Attempt to access the command prompt normally, through the use of a Windows desktop shortcut, and through the use of Batch scripts. If successful, previous successful bypasses should now result in “The command prompt has been disabled by your administrator” messages.

See What We Can Do For You
Download a sample penetration test report to see the results we can deliver for your organization.
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.
