What is the purpose of a pentester certification? What should you know? What should you be able to do? If you pass a TCM exam, you can rest assured that you can do what a pentester does – because you did it during the exam.
Our associate-level pentest exam, The Practical Junior Penetration Tester (PJPT), requires you to conduct an internal pentest.
Our professional-level exam, The Practical Network Penetration Tester (PNPT), consists of an external penetration test.
And in both cases, you write a comprehensive report and present a debrief because that’s what penetration testers do in the real world. You don’t go in blind, and it isn’t pay-to-win as we provide all the training necessary to accomplish everything that is asked of you, and by the end, you will have the experience of doing what a professional pentester does.
Below, we have laid out the TCM pentester certification path that can teach and test an aspiring ethical hacker with little to no IT knowledge (but plenty of dedication and curiosity) until they are able to conduct a penetration test on their own.
Our Teaching Methodology
Our course creators have worked hard to provide a streamlined learning experience with on-demand video instruction paired with hands-on labs that present the necessary practical knowledge and skill development without unnecessary information. Our goal is the most efficient use of time for the greatest return in skill gains for those who want to work in cyber security.
Note: There is a LOT of information out there, so having a curated list of the most relevant and helpful ethical hacking learning sources would be nice. So, of course, Heath Adams has compiled such a deep dive into some beneficial resources in his annual How To Become An Ethical Hacker In 2025 blog post. While our certifications can be completed without outside sources, learning to research and stay curious will serve you well as you progress.
TCM’s Penetration Tester Roadmap
Now lets take a look at the training path of the penetration tester (ethical hacker, white hat hacker, etc). This is the origin story of The Cyber Mentor and one of the more mythologized and sought-after roles in the industry. The goal of the penetration tester is to safeguard an organization by ‘thinking like a bad guy’ in order to find the holes and cracks in a system’s defenses. A curious, creative mind and a persistent attitude are a few of the intangible qualities that are crucial for success as an ethical hacker. So, if you are starting from an ‘absolute newbie’ position, this is our suggested path.
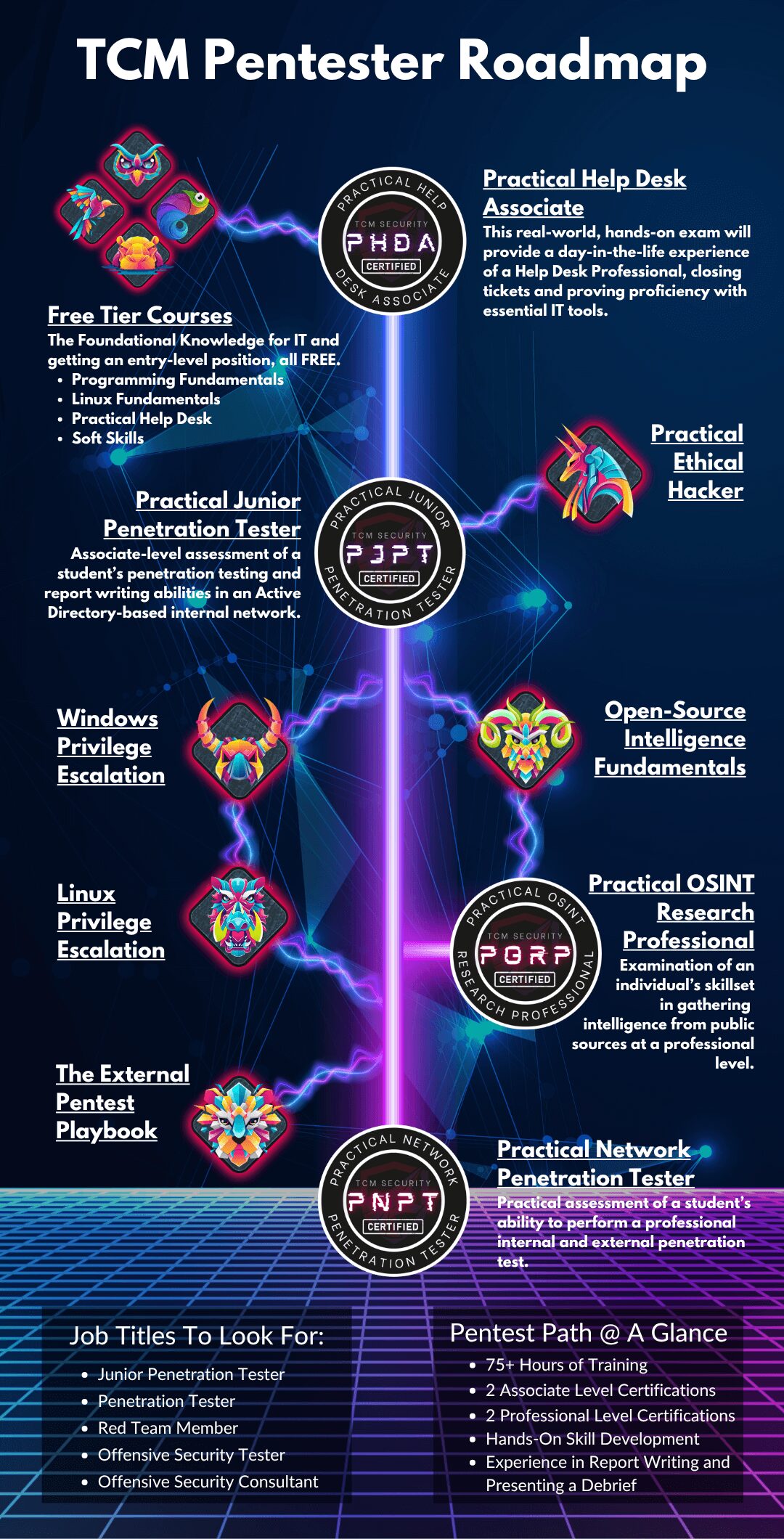
‘Zero’ to ‘Entry Level’ IT
Moving from ‘average digital native’ to ‘professional ethical hacker’ is quite a leap and could lead to motivation-killing disappointments without the proper foundation. One of the tenets of ethical hacking is understanding the system in order to break it. Without that knowledge, you could still watch tutorials on how to run pentesting tools and execute largely automated attacks, but this will only get you so far.
The free tier represents the bedrock layer of TCM courses that provide the training and experience that can take you from basic computer knowledge to Help Desk Technician (don’t sleep on the help desk as a starting point) as a means of gaining practical experience.
This series consists of four courses that cover the basics of programming, the Linux operating system, how to thrive in a Help Desk role, and soft skills for interviews and the workplace.

Programming 100 | 3+ hours
While you do not need to be a programmer to work in cyber security, a basic understanding of coding is all but required for the technical roles in the field. This course uses the Python programming language to ease you into the world of code and will give you the knowledge necessary to progress in other areas.

Linux 100 | 2+ hours
Most of the population that interacts with computers on a daily basis knows the Windows and Mac operating systems, but in IT and cyber security, you need to be able to operate in a Linux environment. This course brings you up to speed on the basics of Linux and prepares you for the other courses where Linux knowledge will be required.

Soft Skills for the Job Market | 7+ hours
Getting an interview requires a good resume or networking. Doing well in the interview requires knowledge of the job and soft skills. This course is designed to equip job seekers with skills in resume writing, professional communication and etiquette, job-hunting tactics, interview preparation, and strategies for standing out in a sometimes crowded market.

Practical Help Desk | 16+ hours
The crowning jewel of our free tier offerings, this course equips the student to get an entry-level IT job at the help desk level. “Breaking into the industry” is commonly viewed as one of the more difficult stages in a cyber security career and help desk jobs are some of the most plentiful roles in the market. Help desk jobs also enable you to gain on the job experience in IT, which can put you on another level when looking for more advanced roles later on. We also offer a certification, the Practical Help Desk Associate, if you want to prove your skills and start your cybersecurity career in an IT support role.

Practical Help Desk Associate (PHDA) | 8 hour exam + Documentation report
The capstone of our free-tier entry-level IT courses, the Practical Help Desk Associate certification validates your expertise in providing real IT support, problem-solving, and customer service. The unique exam style simulates an 8-hour workday in the life of a Help Desk Professional, with a realistic testing environment and IT support tickets to triage, research, close, and document, including a professional report. By passing this certification exam, the student proves their ability to perform the duties required in most Help Desk roles from day one.
Expansion:
We are currently rolling out a Practical Security Fundamentals course that covers the most basic levels of cybersecurity with several modules already available for Academy subscribers, and we plan to add a networking course in 2025 that will provide the basics required to move forward as an ethical hacker.
‘Entry-Level’ to ‘Certified Associate Pentester’
Once you have your basics in hand, TCM offers a straight path to associate-level training and certification to progress in the realm of pentesting. One of our core principles in training and certification is making the most of the student’s time. It is easy to go down rabbit holes in cyber security so we focus on giving you the necessary knowledge and teaching the necessary skills to put you in a good position and start you on your journey of learning ethical hacking.
This level consists of a one-two combo of our most popular training, the Practical Ethical Hacking course, which will provide the essentials of your ethical hacking training and our associate-level pentesting certification in the PJPT.
Practical Ethical Hacking (PEH) | 20+ hours
When people think of “TCM training,” the PEH is usually the course that comes to mind. The brain-child of Heath Adams, this course quickly advances the student through the necessary domains of what it takes to actually function as an ethical hacker, not just the feature film moments.
If you speak to most in the field, they will generally agree that much of pentesting is actually documentation and writing reports, so getting some clear and honest guidance on those topics will put you in a good position to accomplish the day-to-day duties of an ethical hacker.
Practical Junior Penetration Tester (PJPT) | 48 hours practical exam / 48 hours report writing
This certification is TCM’s standard for an ‘entry-level’ ethical hacker. Completing this certification signifies that you have the knowledge and skills to conduct a penetration test in an associate-level capacity. It requires the understanding and use of methodologies and tools that are used every day by professional pentesters.
If you have been pursuing this path for any amount of time, you have likely completed other training composed of Capture the Flag (CTF) style modules. This certification is not like that. You will conduct a penetration test on a system (and everything required to do so is taught in the PEH course) and write a report – just as you would do in a real junior pentester role.
Once you have completed this certification, you have TCM’s seal of approval for being capable of executing the responsibilities of a Junior Penetration Tester.
‘Certified Associate’ to ‘Certified Professional Pentester’
The next section of the journey might take a different route for some individuals. You can begin expanding your training and investigate more specific roles and positions in the corners of cyber security. If you still have your sights set on penetration testing, then TCM has several courses and a couple of professional-level certifications that will better establish your skills and demonstrable credentials.
TCM suggests including foundational instruction in some advanced skills to increase your understanding of Windows and Linux, move laterally through those systems, and develop some professional OSINT abilities. This will round out your skill set and lead to our professional pentester certification.
Open-Source Intelligence (OSINT) Fundamentals | 9 hours
Conducting Open-Source Intelligence (OSINT) is a skill that eventually finds its way into the toolkits of most penetration testers. Whether it is stalking employees’ online profiles to craft a better phishing email or learning about an organization’s tech stack through job postings on professional networking sites, OSINT will make your engagements more effective.
Practical OSINT Research Professional (PORP) | 72 hours intelligence gathering + report writing
This professional-level certification will test your investigative abilities in the digital world. Drawing on real-world info sources like social media, public records, and online databases you will gather, analyze, and compile intelligence. The exam validates your ability to conduct OSINT research and professionally report the findings.
Windows Privilege Escalation | 7 hours
Windows is almost certainly the OS environment you will be trying to navigate during most penetration tests, and after gaining initial access, knowing how to elevate that access will be a big part of enumerating the system. This course will teach you some tricks and methods for turning your initial foothold into a lever that will give you more freedom of movement within a Windows-based network.
Linux Privilege Escalation | 6.5 hours
While Windows is the most used environment in enterprise settings, there will be some situations where knowing your way up the access chain in Linux will be crucial for success. High-tech, government, and industries with operational control systems use some form of Linux so having the tools and procedures from this course in your toolbox will help during engagements in those realms.
External Pentest Playbook | 3.5 hours
If you have passed the PJPT, then you know the hands-on keyboard experience of conducting an internal penetration test. Still, there are some dimensions to an external pentest that you will want to be familiar with before moving on. This course will prepare you for an external pentest by walking through some of the techniques and procedures as well as the logistical necessities such as scoping, client communication, proper finding identification, and more.
Practical Network Penetration Tester (PNPT) | 120 hours practical exam / 48 hours report writing
Building on the momentum of the PEH course, PJPT certification, and TCM’s supplemental external pentest instruction, the PNPT represents a professional level of skills and knowledge in executing a pentest.
The practical test measures the student’s ability to conduct an internal and external engagement using techniques and methodologies employed by experienced pentesters, including conducting OSINT, bypassing AV, moving laterally and escalating through the network, and more. This is paired with the ability to record and present the findings in a professional manner, including a live debrief.
This exam provides a total pentest experience that will prepare the student for a real-world engagement from planning to presentation of findings.
Conclusion
Penetration testing is essential for maintaining the digital defenses that keep our information secure and the systems we depend on daily up and running. Vulnerability scans and automated tools are great help, but having a curious, skilled, and determined human test a network’s defenses can reveal gaps in security and might even determine the severity of an eventual breach.
TCM’s mission is to equip those who want to take up this duty and ensure that they have the best chance to succeed in the field by providing actual experience with the entire process of penetration testing.
If you want to learn more about TCM’s path for pentesting preparation, check out the TCM Academy and our certifications. We also offer a PNPT Accelerated Camp, which is a four day live training that will provide extra practice for those looking to pursue the PJPT and PNPT certifications.
Check out this video with Alex Olsen for another perspective on how you can break into penetration testing:
About the Author: Josh Daniels
Josh is an avid storyteller and writer who loves learning about the behind-the-scenes of the digital world we live in. While his professional experience is in content marketing, Josh began pursuing a career in cybersecurity in 2022, gaining a Sec+ certificate along with other training from industry professionals and a life long learner attitude.
When he is not writing, Josh enjoys outdoor adventures with his family, watching movies, reading, and an unofficial (unpaid) side gig as a Game Master Consultant for several friends who play table top RPGs. At TCM, Josh has found a home where his passion for storytelling and cybersecurity meet.
“Once men turned their thinking over to machines in the hope that this would set them free. But that only permitted other men with machines to enslave them.”
– Frank Herbert
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcm-sec.com/our-services/
Follow Us: Email List | LinkedIn | YouTube | Twitter | Facebook | Instagram | TikTok
Contact Us: [email protected]
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.










