In this blog TCM’s pentest lead Aaron Wilson will cover the hardware, software, report templates, and other infrastructure considerations that make a pentest firm run smoothly.
The Basics
Report Templates
For a small penetration testing firm of 1-5 employees, the most important thing to have at this level is a few report templates for your various types of tests. These templates will save you time and effort when creating reports for your clients. I would recommend having a rough template for these three types of tests:
- External Penetration Test
- Internal Penetration Test
- Vulnerability Scan Report
These are the three most common types of tests you are likely to conduct while working at or running a small pentesting consultancy. If you specialize in certain types of tests that are unique, and you know you will be writing those reports frequently, make yourself a template for the most common tests that you expect from your clients!
Vulnerability Scanners
For other equipment you should have a paid or free vulnerability scanner for example OpenVAS, Tenable Nessus, or Qualys are some popular options. Depending on the amount of money you would like to spend you can self-host a vulnerability scanning server or use a cloud provider for your server.
Dropboxes
Finally, if you are working on internal penetration tests for clients, it’s very likely that you will need to send a device to their network to perform the testing. This is sometimes called a “dropbox”, “drone” or “client device”. You can purchase something like an Intel NUC (https://www.amazon.com/Intel-NUC-NUC13ANHi3-Barebone-System/dp/B0C7MVLWYW), Raspberry Pi-style device, or a full-sized laptop.
To access these devices, you will need a networking protocol that allows your device and the remote device to communicate. Some of the most common options that pentesting firms utilize are Tailscale or Zerotier. These are paid options, but another free less commonly known option is Google Remote Desktop. You simply install a remote desktop Chrome extension to the device browser and you can access your devices anytime and from anywhere from a single Google account.
Dropbox OS Recommendations
I highly recommend running Windows with a guest Kali Linux virtual machine on the devices sent to clients. Windows will allow you the flexibility to perform some Windows-based attacks while also having the flexibility and customization of Linux. Don’t forget to use PimpMyKali on the Kali Linux virtual before it arrives at the client site, this will get you pre-loaded with all of the tools you will need.
Advanced Infrastructure, Stage 1
When a team expands to over five people, it’s time to start considering a more significant infrastructure investment.
This should include the following:
- Reporting Tool
- Paid Vulnerability Scanner
- Internal Git Repository
- Additional Dropboxes for Client Sites
- Phishing Server for Social Engineering
Let’s talk about why each of these pieces of infrastructure is important.
Reporting Tools
At this point in your team’s development, you will probably be collaborating on different types of assessments while also managing a high number of clients. A reporting tool is vital for keeping all of your reports similarly formatted and saves time by having pre-templated issues. There are many, many options out there for collaborative penetration testing tools such as Plextrak, Dradis, AttackForge, and others. I’d recommend looking into a few vendors to see what fits your budget and requirements.
Vulnerability Scanners
A Vulnerability Scanner is a crucial component for quickly identifying low-hanging fruit during external and internal security assessments. There are also many paid and free vulnerability scanning tools available, which I have mentioned above in the prior section.
Code Repository
An Internal Git Repository is a great resource for a growing team. A mature penetration testing team should be writing tools, automations, and templates to make their life easier. This tool can be used to host automated scripts for building machines, custom-written tools and scripts, or even custom wordlists of common passwords from your engagements. It is important to have this proprietary code and information available to your penetration testing employees. Everyone loves sharing tools with others, but I would recommend only making certain tools and scripts publicly accessible by having a separate public repository for sharing your best work that other penetration testers would find valuable.
Phishing Server
Depending on the types of assessments you offer, it may be wise to have a phishing server for social engineering engagements. Using AWS or other cloud providers, this server can be publicly hosted on the internet for your social engineering victims to access. Using AWS, you can share access to the server with your team members using an SSH Private key, a shared username/password, or via AWS Cloud Connect. This server can be used for different domains as you perform your campaigns with minimal changes between client engagements.
Diagram of a Basic Pentest Firm Infrastructure

Advanced Infrastructure, Stage 2
For advanced penetration testing teams, I would recommend a few additional infrastructure components.
- Reporting Tool
- Vulnerability Scanner
- Internal Github Repository
- Dropboxes for Clients
- Phishing Server
- Password Cracking Server
- C2 Infrastructure
- Logging and Monitoring
Password Cracking Server
A great addition for any penetration testing team is to have a beefy password cracking server. This server can be a super powered machine with multiple graphical processing units (GPUs). Additionally, as you crack client passwords in engagements the hashes will automatically be added to the server’s hashcat.potfile. This means that future passwords you identify in client environments may be cracked instantly once the hash is identified in the potfile.
C2 Infrastructure
The next addition for an advanced team is a C2 (Command and Control) Infrastructure. There are lots of free options available for C2 infrastructure, including famous free tools such as Merlin, Sliver, and Caldera. There are also several paid options such as Cobalt Strike, Voodoo, and Scythe. A nice collection of C2 options can be found here: https://github.com/tcostam/awesome-command-control?tab=readme-ov-file.
Having a mature C2 infrastructure will require specialized skillsets on your team, such as someone to manage the infrastructure itself and someone to develop specialized or encoded payloads for dropping on endpoints during engagements.
Logging, Monitoring, and Alerts
Finally, a mature team should be utilizing “secure by design” concepts and enforcing logging and monitoring on all machines deployed to client environments and within their infrastructure. This will prevent and monitor for malicious activity if a threat actor were to gain access to your infrastructure.
There have been multiple instances of advanced teams having their tooling leaked during engagements by threat actors. One of the most famous instances of this was the “Shadow Brokers” hack in 2013, which ultimately leaked several NSA tools to the internet. There are many options for logging and monitoring infrastructure, but one of the easiest to set up is Wazuh. TCM Security has featured many videos with Wazuh. Other options may include Splunk, Elasticsearch, or syslog-ng.
Defense in Depth
Taking the previous concept a step further, a mature team may choose to implement MFA to access all environments, and if you really want control, consider implementing a full Active Directory environment that testers must utilize when accessing the infrastructure.
Diagram of an Advanced Pentest Firm Infrastructure
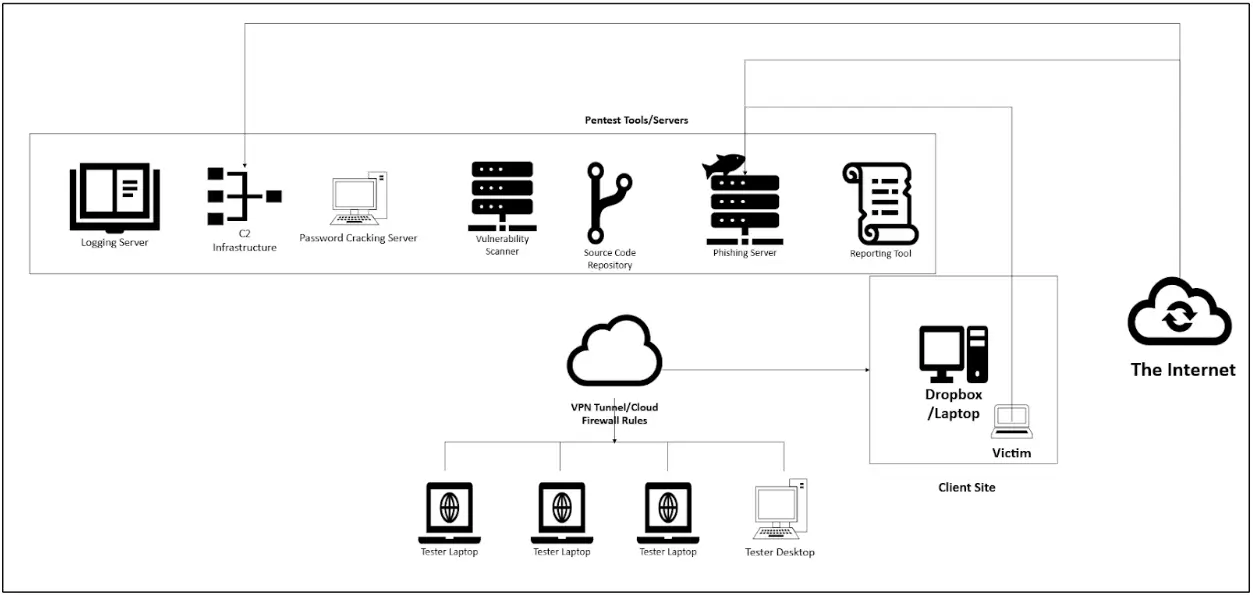
Conclusion
This list is not exhaustive, but should give you a good idea of the hardware, tools, and procedures that are necessary for running a pentest firm, as well as some advanced options for growing teams. If you are looking for training resources for junior members or advanced/tangential training or certification for yourself or your team, check out the TCM Academy and Certifications for hands-on, practical training and testing.

About the Author: Aaron Wilson
Aaron is a passionate security professional with experience in the Fortune 50. He is the Red Team Lead at TCM Security, responsible for leading the penetration testing and consulting teams. He is also an avid Capture the Flag Creator and has published multiple rooms on TryHackMe. Aaron is also CEO and Founder of the Wilson Security Group and publishes videos on YouTube on security topics and cybersecurity certification reviews.
Aaron holds certifications such as the eMAPT, CISSP, eCPPTv2, eWAPTv2, CEH, and eJPT certifications among others. He holds a bachelor’s degree in Security and Risk Analysis from Penn State University as well as a Master’s in Information Assurance and Cybersecurity from Western Governor’s University (WGU).
Follow Aaron on Social Media:
LinkedIn – https://www.linkedin.com/in/wilson-security
YouTube – https://www.youtube.com/c/WilsonSecurityGroup
TryHackMe Hacker Methodology – https://tryhackme.com/r/room/hackermethodology
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcm-sec.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: [email protected]
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

