DeepSeek and You Shall Find:
Automating Pentest Reports with AI-Powered Templates for 63 Cents
Since the dawn of time, reporting has been the bane of every pentester’s existence. It’s often the most tedious part of the job and is almost always highlighted as something to watch out for when first entering the field. Fortunately, in 2025, we now have the advantage of AI, our own personal language expert to help lighten the load.
In this blog, we’ll show how to generate pentest finding templates with DeepSeek AI using MITRE’s Common Weakness Enumeration (CWE) categories. We’ll also build a wrapper script to automatically import these templates into SpecterOps’s reporting tool, GhostWriter.
If you would like to see a deep dive into an example pentest report, TCM’s pentest lead, Aaron Wilson, breaks down “what is a pentest report?” in another blog.
To learn more about the other aspects of pentest report writing, the Practical Network Penetration Tester certification not only proves your technical skill but also your administrative capabilities, such as report writing.
The Pain of Pentest Reporting
Ask any pentester what the least enjoyable part of their job is, and reporting almost always tops the list. While finding vulnerabilities is the exciting part, the reality is that none of it matters if it can’t be clearly communicated to the client. That’s where reporting comes in.
Unfortunately, reporting tends to be:
- Repetitive – Many findings show up again and again across different clients, meaning pentesters often rewrite the same descriptions, impacts, and remediations from scratch.
- Time-consuming – A single report can take hours or even days to polish, often extending long after the technical work is done.
- Mentally draining – After an intense engagement, switching gears from creative problem-solving to formal documentation can feel like a grind.
- High stakes – Clients rely on these reports to prioritize fixes and justify security spend, so accuracy and clarity are critical.
The paradox is that reporting is both the most tedious and the most impactful part of the job. A pentester can do world-class technical work, but if the report is unclear, inconsistent, or rushed, the value of that work is diminished.
Templating Findings with AI
Finding templating is a core feature in nearly every pentest reporting tool. It allows pentesters to create reusable boilerplate findings that cover common vulnerability types, saving time and ensuring consistency. MITRE’s Common Weakness Enumeration (CWE) categories are especially well-suited for building these templates, since they abstract vulnerabilities into well-defined classes. From there, each template can be tailored on a case-by-case basis, adding nuance and context as needed.
This is the type of work in which AI excels. Taking structured inputs like CWE categories and transforming them into clear, professional, and repeatable templates. Instead of spending hours drafting boilerplate language, pentesters can offload the heavy lifting to AI and focus their time on refining the details that truly matter to each engagement.
So the question becomes, how do you get AI to generate a high-quality template? The answer is a bit nuanced. Sure, a simple prompt like “Write me a pentest finding for CWE-78” can produce solid results, but the real key lies in defining your goals and requirements for the template.
Consider the details you need to include, such as: Do you use CVSS 3.1 for risk scoring? Do you rely on an impact-and-likelihood risk matrix? What additional data should be captured? Are there reference materials or resources that should appear in every finding? These are all specifics you can’t assume the AI will know on its own. You need to guide it so the output matches your standards clearly.
Building the AI Wrapper Script
The first thing needed before we even start prompting the AI is a way to create findings programmatically via our pentesting reporting tool. This will vary based on the reporting tool used. In this example, I will use SpecterOps’s GhostWriter.
For this use case, our goal will be to have the following information filled out in our finding template:
- Finding Title
- Finding Type ID – This is a Ghostwriter-specific field that defines the finding type
- Description
- Impact – This should be formatted in the following manner:
- Likelihood: <Low, Moderate, High, Very High>
- Impact: <Low, Moderate, High, Very High>
- Mitigation
- References
- cvssScore
- cvssVector
- SeverityId
- Extrafields
- Table description (short version of the remediation)
- Tools (tools used in the finding)
GhostWriter exposes a GraphQL API that allows findings to be inserted programmatically. Here’s an example mutation that maps directly to the fields above:
mutation MyMutation {{
insert_finding(objects: {{
title: "{cwe['title']}",
findingTypeId: "{cwe['findingTypeId']}",
description: "{cwe['description']}",
impact: "<p><strong>Likelihood:</strong> {{Low, Moderate, High, Very High}} – {cwe['likelihood']}</p>\r\n<p> </p>\r\n<p><strong>Impact:</strong> {{Low, Moderate, High, Very High}} – {cwe['impact']}</p>",
mitigation: "{cwe['mitigation']}",
references: "{cwe['references']}",
cvssScore: "{cwe['cvssScore']}",
cvssVector: "{cwe['cvssVector']}",
extraFields: {{
tabledescription: "{cwe['extraFields']['tabledescription']}",
tools: "{cwe['extraFields']['tools']}"
}},
severityId: "{cwe['severityId']}"
}}) {{
affected_rows
}}
}}Since GhostWriter uses HTML for formatting, you’ll notice raw HTML included in the impact field. This ensures the imported finding renders with the correct formatting inside the report.
Step 1: Test the API
Before writing any AI integration, it’s best to confirm that you can successfully ingest findings through the API. Below is a simple Python function that accepts a JSON object containing the finding details and pushes it into GhostWriter:
def ingest_into_ghostwriter(cwe):
hasura_admin_secret = ""
ghostwriter_endpoint = {}query = f"""
mutation MyMutation {{
insert_finding(objects: {{
title: "{cwe['title']}",
findingTypeId: "{cwe['findingTypeId']}",
description: "{cwe['description']}",
impact: "<p><strong>Likelihood:</strong> {{Low, Moderate, High, Very High}} – {cwe['likelihood']}</p>\r\n<p> </p>\r\n<p><strong>Impact:</strong> {{Low, Moderate, High, Very High}} – {cwe['impact']}</p>",
mitigation: "{cwe['mitigation']}",
references: "{cwe['references']}",
cvssScore: "{cwe['cvssScore']}",
cvssVector: "{cwe['cvssVector']}",
extraFields: {{
tabledescription: "{cwe['extraFields']['tabledescription']}",
tools: "{cwe['extraFields']['tools']}"
}},
severityId: "{cwe['severityId']}"
}}) {{
affected_rows
}}
}}
"""post_data = {
"query": query
}
print(json.dumps(post_data, indent=2))
headers = {"Content-Type":"application/json","X-Hasura-Admin-Secret":hasura_admin_secret}
response = requests.post(f"https://{ghostwriter_endpoint}}/v1/graphql",json=post_data,headers=headers,verify=False)
print(response.json())if "errors" in response.json().keys():
if "Uniqueness violation" not in response.json()['errors'][0]['message']:
f = open('failed_imports.txt','a')
f.write(cwe['title']+"\n")
f.close()Step 2: Generate JSON with AI
The next objective is to generate a prompt for the AI that will output a JSON object with the exact fields we need to ingest into our GraphQL mutation. The following prompt is an example of one that will output the data in our expected format. It also provides some additional requirements for the AI. These should be tweaked based on your requirements.
Can you give me a pentest report template for CWE-78 in the following json format?{
title: "{title}",
findingTypeId: "{findingTypeId}",
cvssScore: "{cvssScore}",
cvssVector: "{cvssVector}",
description: "{description}",
likelihood: "{likelihood}",
impact: "{impact}",
mitigation: "{mitigation}",
references: "{references}",
extraFields: {
tabledescription: "{description_short}.",
tools: "{tools_used}"
},
severityId: "{severity}"
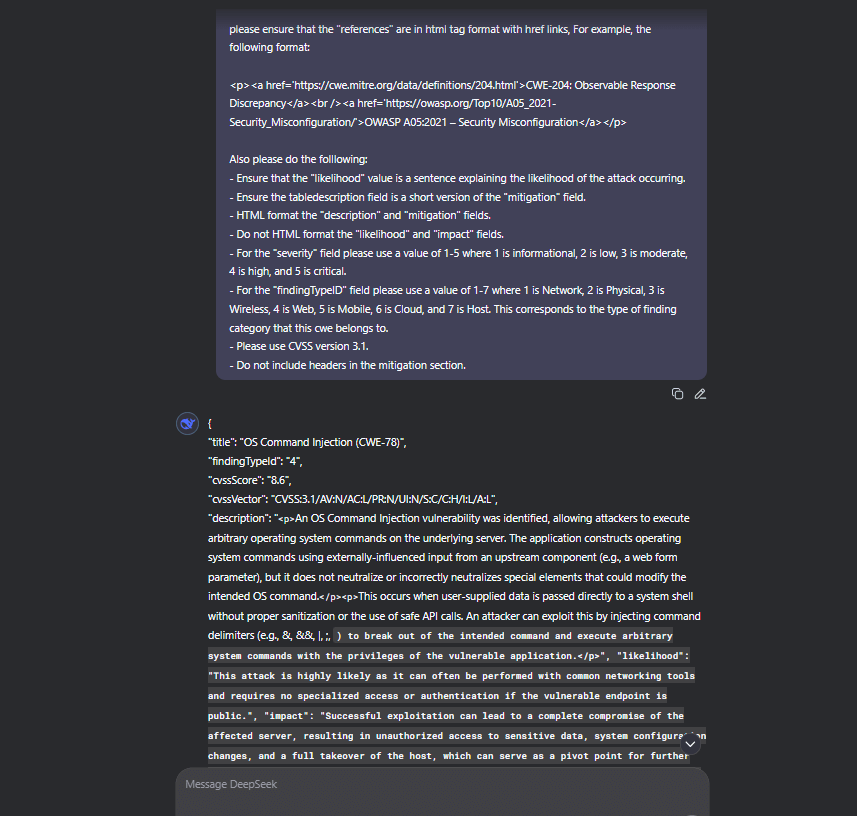
}please ensure that the "references" are in html tag format with href links, For example, the following format:<p><a href='https://cwe.mitre.org/data/definitions/204.html'>CWE-204: Observable Response Discrepancy</a><br /><a href='https://owasp.org/Top10/A05_2021-Security_Misconfiguration/'>OWASP A05:2021 – Security Misconfiguration</a></p>Also please do the folllowing:
- Ensure that the "likelihood" value is a sentence explaining the likelihood of the attack occurring.
- Ensure the tabledescription field is a short version of the "mitigation" field.
- HTML format the "description" and "mitigation" fields.
- Do not HTML format the "likelihood" and "impact" fields.
- For the "severity" field please use a value of 1-5 where 1 is informational, 2 is low, 3 is moderate, 4 is high, and 5 is critical.
- For the "findingTypeID" field please use a value of 1-7 where 1 is Network, 2 is Physical, 3 is Wireless, 4 is Web, 5 is Mobile, 6 is Cloud, and 7 is Host. This corresponds to the type of finding category that this cwe belongs to.
- Please use CVSS version 3.1.
- Do not include headers in the mitigation section.This produces promising results that output a JSON object in the exact format required to execute the GraphQL query. We can programmatically loop this query and numerically go through a large number of CWEs to automate our pentest report template creation. The full POC code for this can be found here.
Results
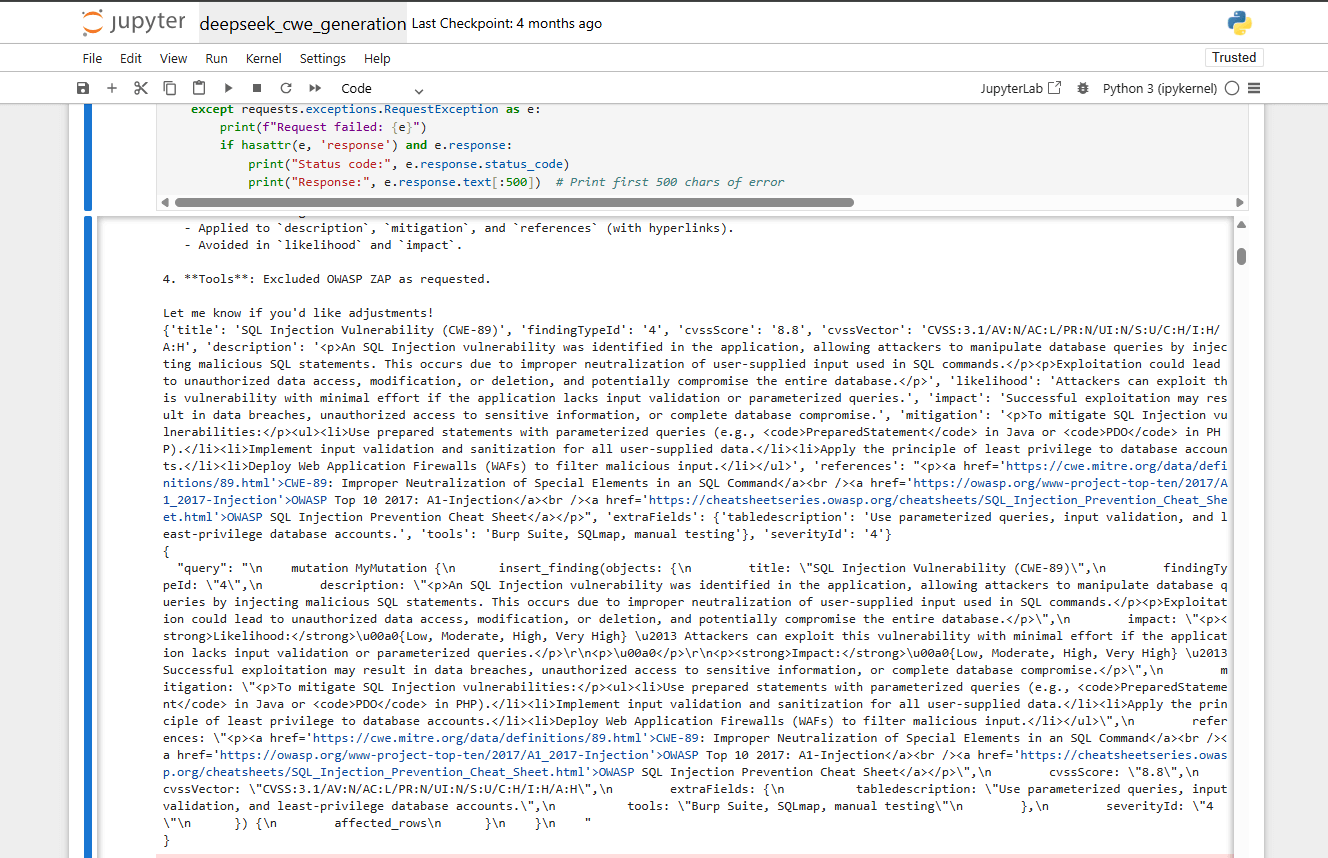
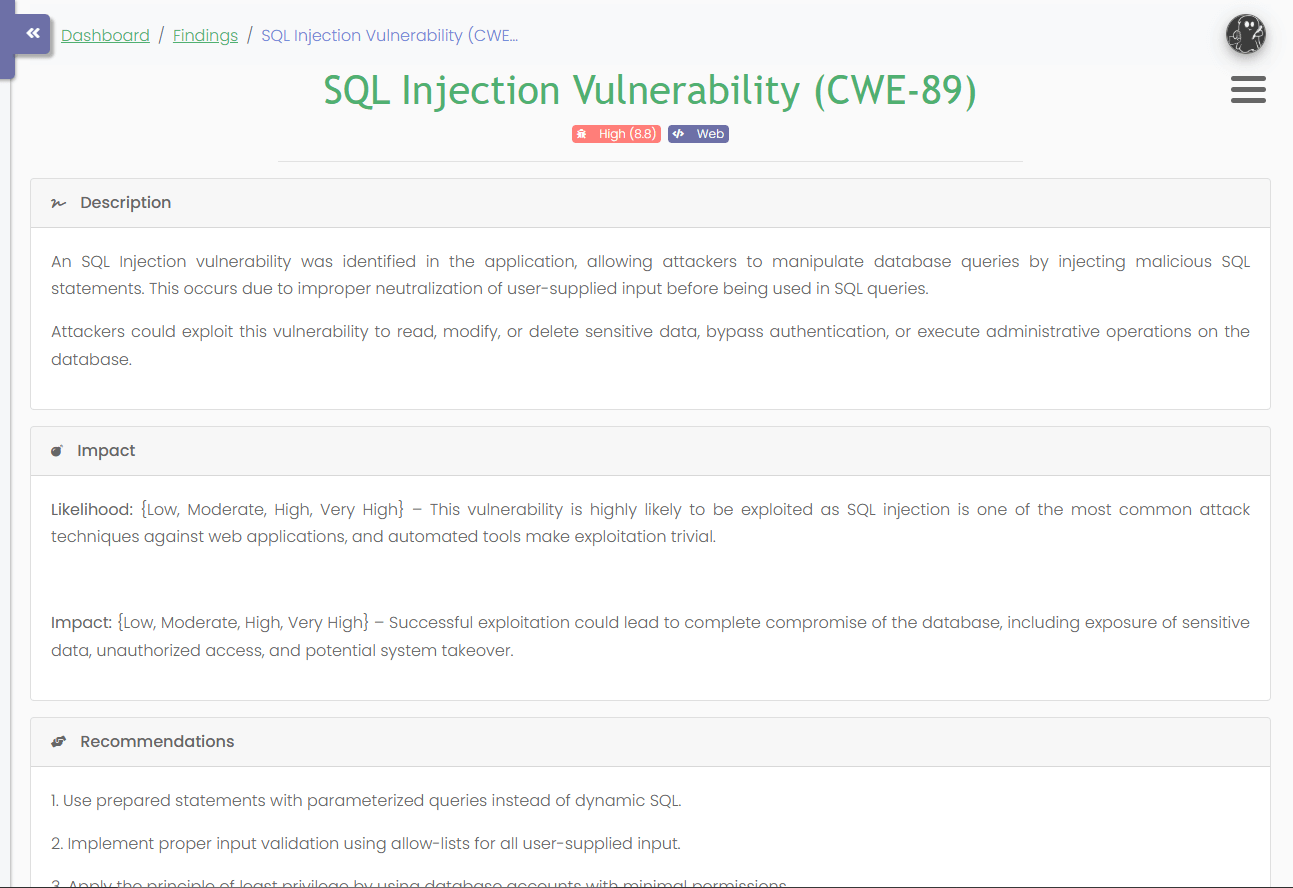
From the screenshots above, you can see the code output as well as the successful import of CWE-89. For demonstration purposes, I ran this script up to CWE-999 with great success.
This workflow demonstrates how AI can automate repetitive, time-consuming tasks and produce fast, consistent, and highly usable output for pentest reports.
Return on Investment
One of the most compelling benefits of using AI for pentest finding templates is the clear return on investment. In the example above, generating 1,000 CWE templates cost me just $0.63, a negligible expense compared to the time and money required to create them manually.
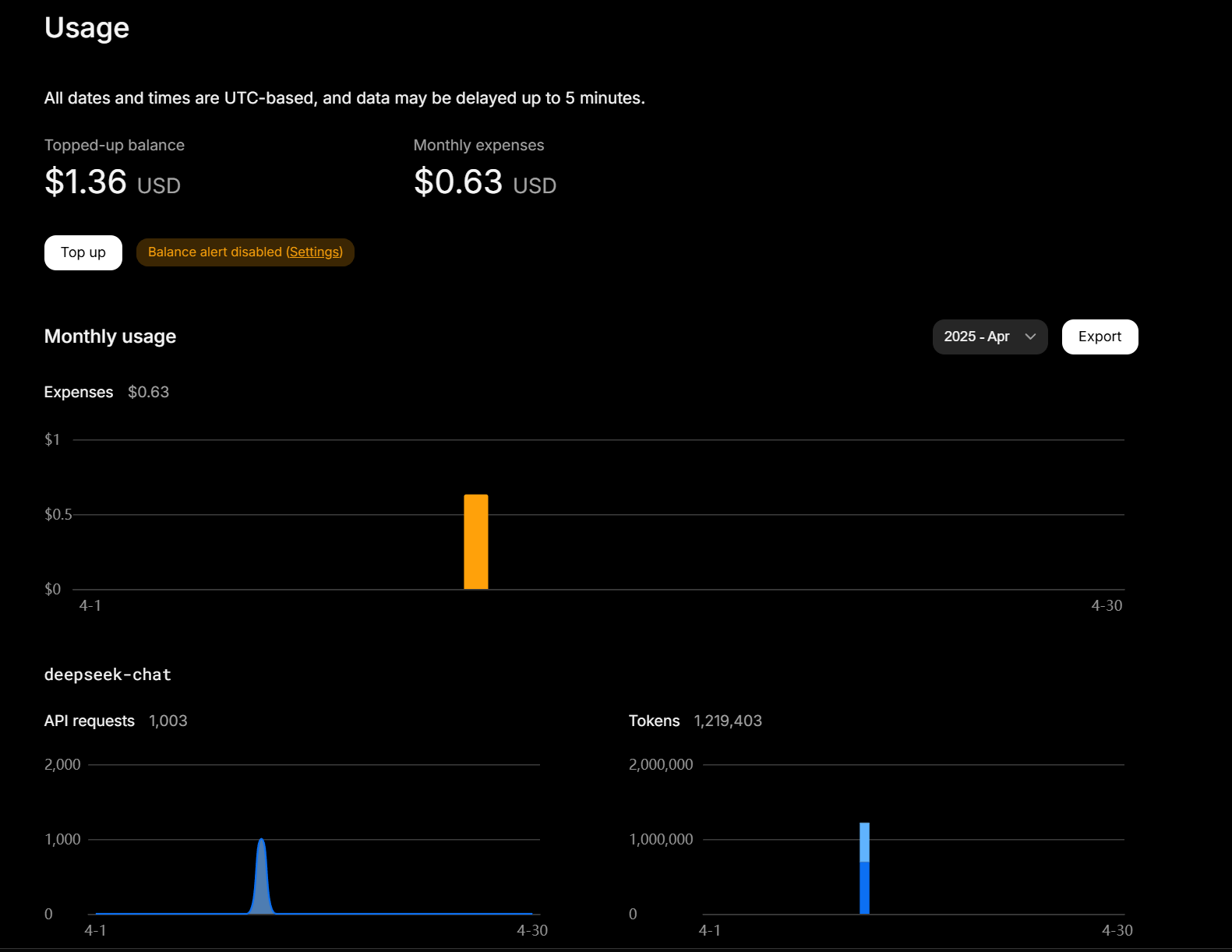
To put this into perspective, let’s say a pentester has the bandwidth to create four templates an hour. To create 1000 templates, it would take them 250 hours. Additionally, let’s say the pentester costs the business $70 an hour. This would cost the business $17,500 in billable hours.
This demonstrates that AI not only dramatically speeds up the reporting process but also delivers a tangible financial advantage. What would have taken hundreds of hours and thousands of dollars can now be accomplished in minutes for less than a dollar.
Conclusion
AI can be an incredibly powerful tool across all professions, streamlining repetitive tasks and freeing up valuable time. What once took hundreds of hours can now be completed in minutes for just a few cents, allowing pentesters to focus on the technical work that truly matters.
While AI isn’t perfect, the return on investment is undeniable when it comes to time saved. Templates and outputs still require human review to refine the details, and every AI-generated finding should be carefully checked and tailored before being delivered to a client.

About the Author: Jason Marcello
Jason is a Principal Offensive Security Engineer at TCM Security with a deep passion for all things cybersecurity. Jason has professional experience in the healthcare, banking, and tech industries. He specializes in web application security and is especially passionate about research topics pushing the boundaries of application security. Jason holds a Bachelor of Science in Computing Security from Rochester Institute of Technology. Additionally, Jason holds several industry-recognized certifications such as the OSCP, OSWE, OSEP, OSWA, PWPP, BSCP, CRT, CRTO, etc.
Jason is also a husband, dad of two dogs, and a coffee/espresso aficionado. In his free time, he enjoys hiking, gaming, and playing guitar.
Social Media Links:
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcm-sec.com/our-services/
Follow Us: Email List | LinkedIn | YouTube | Twitter | Facebook | Instagram | TikTok
Contact Us: [email protected]
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

