Credential stuffing remains one of the most efficient paths to account takeover, and AI assistance is changing the economics and effectiveness of those attacks. Below is a practitioner-focused examination of how the classic stuffing workflow works, how AI augments it, what to test for as a pentester, and what defenders should harden, grounded in Verizon’s 2025 DBIR and established operational guidance.
AI is an excellent tool for automation, efficiency, and speed, not just for Fortune 500 companies but also for anyone with a computer and a network connection. If AI allows for scaling of these attacks, you better believe that threat actors, ransomware groups, and black hats will be making use of the technology. So, as an offensive security professional you will want to replicate those methods as closely as possible to provide your clients with the best visibility into the security of their networks. Likewise, if you are responsible for analyzing/preparing network defense, you will want to know what to expect. What are the capabilities of AI, and how can they be deployed?
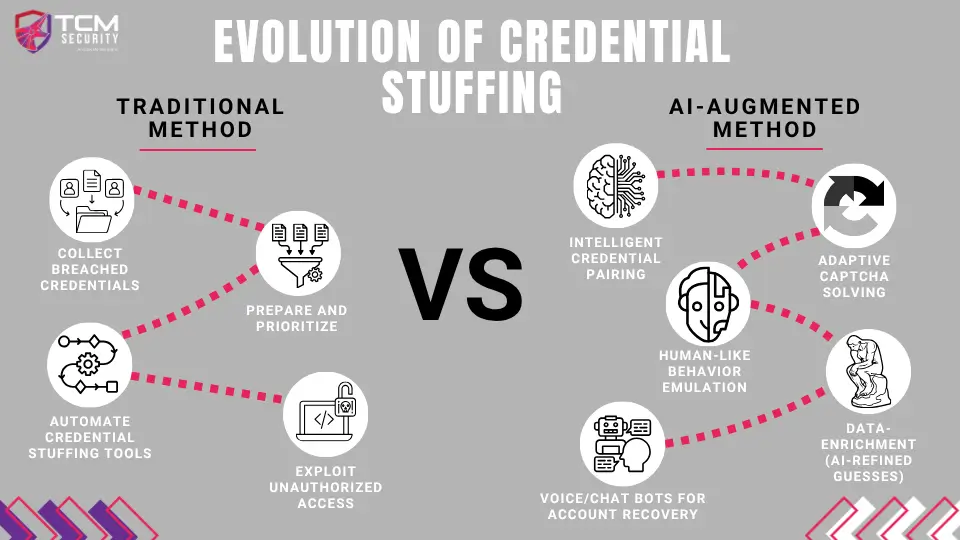
Traditional Methods for Credential Stuffing
Credential stuffing is the automated use of leaked username:password pairs against other sites and services to achieve account takeover. Attackers gather “combo lists” from breaches or malware, clean/prioritize them, and run mass login attempts against targets using commodity tools and proxy pools. The 2025 Verizon DBIR shows that 88% of breaches in 2024-2025 used stolen credentials to bypass a network’s layered security. Credential abuse remains a leading initial access vector (roughly 22% of breaches in 2024–25), and stolen credentials factor heavily in web-app attacks.
Typical traits of traditional stuffing: high volume of low-effort attempts, reliance on password reuse, simple automation (Sentry MBA / custom scripts), and evasion via proxies and basic rate-limiting bypasses. See OWASP’s credential-stuffing guidance and OAT taxonomy for technical details and standard defenses.
How AI Augments The Traditional Process
AI doesn’t replace the old playbook, it amplifies and force multiplies the effort in several concrete ways:
- Intelligent credential pairing: ML/LLM models infer likely email patterns and password variants (e.g., surname+year → Surname2023), expanding hit rates beyond raw leaked combos.
- Adaptive CAPTCHA / challenge solving: Vision models and specialized solvers make bypass of image/text CAPTCHAs more reliable.
- Human-like behavior emulation: LLMs + orchestration randomize timing, device fingerprint headers, mouse/touch patterns, and navigation flows to mimic legitimate users, defeating simple behavioral heuristics.
- OSINT enrichment: LLMs synthesize public profile data (usernames, company structures, social handles) to prioritize high-value targets and craft social-engineering vectors for account recovery.
- Automated account recovery abuse: AI chat/voice agents can be used to script convincing account recovery calls or chat interactions to manipulate support personnel or IVR systems.
These AI augmentations increase success rates while reducing the skill barrier, which in turn helps explain the DBIR findings that credential-based attacks continue to dominate web application compromises.
How Pentesters Can Use AI To Model Adversary Capability
As a pentester or red teamer, your goal is to emulate the capability of modern attackers so that defenders of organizations see realistic risk. Some practical steps that AI can be used to increase effectiveness are:
- Use enriched combo lists: augment breach dumps with username variants and contextual transformations (append likely birth years, company initials). This models intelligent credential pairing.
- Simulate human-like clients: rotate user-agents, vary request timing, and emulate device fingerprint headers to test behavioral analytics. Make sure your agreed-upon scope allows this level of simulation.
- Test account recovery flows: emulate voice/chat social engineering against helpdesk/IVR and verify whether weak answers or LLM-synthesized responses could succeed.
- Measure detection windows: run controlled stuffing with low volumes across distributed proxies to observe detection thresholds and alerting latency. Capture logs to show which signals (IP, UA, timing) triggered detection or escaped it.
- Report exploitability & business impact: quantify successful takeovers, downstream fraud risks, and what sensitive actions were possible (fund transfer, SSO pivot, admin access). Use these operational details to prioritize fixes.
* When practicing these techniques, follow strict rules of engagement, notify stakeholders, and always avoid persistent account compromise or data exfiltration beyond scoped tests.
Defensive Measures Against Credential Stuffing
Whether you are an offensive tester making suggestions for a client or a defensive security analyst/engineer looking to tighten up your organization’s environment, there are a few measures that can be taken to harden against these kinds of attacks.
Preventing Credential Stuffing
As suggested by OWASP, MFA, while not a silver bullet, is a challenging hurdle for attackers to overcome and should be used wherever possible to make a potential credential stuffing attempt more of a hassle than the majority of minor threat actors are willing to work around.
Device fingerprinting for a user by pulling some data from HTTP headers, such as: Operating system & version, Browser & version, Language, can be enough to detect some less sophisticated attempts at using stolen credentials.
Blocking known compromised credentials from the bevy of username:password combinations that have been published through data breaches is another good step toward defending.
There are other strategies as well, and while none of these options is a sure-fire method on its own, developing a defense-in-depth strategy allows several opportunities for attackers to get caught trying to pass themselves off as a legitimate user.
Detecting Credential Stuffing
While User Entity Behavior can be imitated with the use of AI, AI can also be used to quickly determine anomalies in geolocation, impossible travel, and time discrepancies. Rate-limiting and challenge escalation can make the process more trouble than it’s worth and persuade an attacker to move on. Cleverly baited Honey Pot credentials using a set of breached credentials connected to a high-value person within the organization, can send up a flare early in a potential attack.
What This Means Moving Forward
Defenders and attackers will both increasingly leverage AI. That creates an arms-race dynamic: AI will make attacks cheaper and more tailored, but also enables more sophisticated defense analytics. Offensive professionals will need to stay on top of the latest and most efficient AI supplements, since that is what adversaries will be using. For defense, prioritize identity hygiene, reduce reliance on passwords, and instrument authentication flows for richer telemetry. Verizon’s 2025 analysis serves as a reminder that credentials remain the path of least resistance, making them excellent targets for AI-assisted automation.
Tools & Resources for Pentesters (Starter List)
- OWASP – Credential stuffing guidance & Automated Threats catalog (OAT).
- Akamai / SecOps research – large-scale credential stuffing telemetry and trends (useful for modelling volume & proxies).
- Password breach feeds / monitoring APIs – for realistic combo lists (only use in scoped, authorized tests).
- Browser automation & headless tools – such as Playwright with randomized behavior for human-like simulations.
- Bot management test sandboxes – vendor tools to test bypasses safely (use in coordination with vendors and in scope).
In Closing
Credential stuffing is low-cost, high-impact for attackers, and the lowest hanging fruit is always going to be the first that gets picked by attackers. Using AI only means that this attack vector will be easier for a higher volume of individuals or groups to use when probing the outer defenses of an organization. Pentesters should be well-versed in how to use these new efficiency tactics in order to better emulate attackers and cover more ground for their clients. Defenders also need to be aware of these new tools and tactics in order to mitigate attacks more efficiently and shield their organizations against threats.
TCM offers both defensive and offensive training and certifications that can help you gain a solid foundation in attack and defense methodology, which can then be enhanced through the growing development of AI tools.
About the Author: Josh Daniels
Josh is an avid storyteller and writer who loves learning about the behind-the-scenes of the digital world we live in. While his professional experience is in content marketing, Josh began pursuing a career in cybersecurity in 2022, gaining a Sec+ certificate along with other training from industry professionals and a life long learner attitude.
When he is not writing, Josh enjoys outdoor adventures with his family, watching movies, reading, and an unofficial (unpaid) side gig as a Game Master Consultant for several friends who play table top RPGs. At TCM, Josh has found a home where his passion for storytelling and cybersecurity meet.
“Once men turned their thinking over to machines in the hope that this would set them free. But that only permitted other men with machines to enslave them.”
– Frank Herbert
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers. Pentest Services: https://tcm-sec.com/our-services/ Follow Us: Email List | LinkedIn | YouTube | Twitter | Facebook | Instagram | TikTok
Contact Us: [email protected]
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

