Introduction
Earlier this year I published an OWASP Top 10 2025 prediction blog where I pulled CVE data from 2021 and made data driven predictions on where the new top 10 list will land. Now that the official list has been released, it’s time to reflect on the results of the new list.
Recap of Predictions
To recap, my predictions were the following:
- A01:2025 – Broken Access Control
- A02:2025 – Injection
- A03:2025 – Insecure Design (Combined with Security Logging and Monitoring Failures)
- A04:2025 – Identification and Authentication Failures
- A05:2025 – Cryptographic Failures
- A06:2025 – Security Misconfiguration (SSRF could potentially be combined into here)
- A07:2025 – Vulnerable and Outdated Components
- A08:2025 – Software and Data Integrity Failures
- ?
- ?

The Official OWASP Top 10 2025 List
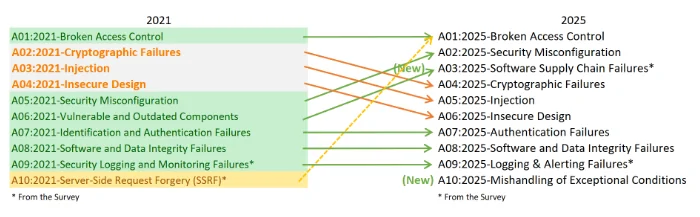
What I Got Right
The following was correctly predicted:
- Broken Access Control remains at the #1 spot.
- Software and Data Integrity Failures remains at the #8 spot
- The majority of categories were represented and OWASP continues to make categories more broad (combining SSRF with the Broken Access Control category).
Broken access control remaining at the #1 spot was definitely unsurprising as that is by far the most common issue I see plaguing web applications. However, I did not anticipate SSRF being combined with this category, but after some thought it does make sense to place it here. The root cause of SSRF relates to an access control failure where users are able to make server-side requests to systems that they should not be able to.
The same categories being reused was also not surprising, as OWASP has kept very similar categories across the years with some slight name adjustments. They also continue to make categories broader, which is why it makes sense that SSRF was combined with another category.
What I Got Wrong
The following are key items that were incorrectly predicted:
- Security Misconfigurations surged to the #2 spot rather than falling down the list.
- Vulnerable and Outdated Components was renamed to Software Supply Chain Failures and jumped up on the list.
- Injection fell to #5 instead of rising on the list.
- Identification and Authentication Failures remained in the same spot rather than rising.
- A brand new category was introduced called “Mishandling of Exceptional Conditions.”
A large portion of the predictions did not come to fruition for several reasons, mainly because OWASP counts each vulnerability category only once per application, regardless of how many individual instances exist. For example, if an application contains a systemic XSS flaw that results in ten separate CVE entries, OWASP still treats it as a single occurrence of that weakness for Top 10 scoring purposes. This methodology emphasizes how widespread a class of vulnerability is across applications, not how many times it appears in any one application.
Additionally, OWASP seems to really emphasize the community when it comes to crafting the new list. To craft my predictions, I worked solely with CVE data, which is obviously not a full representation of what goes into determining these types of lists.
Reflecting on the New List
The rise of Security Misconfigurations to the #2 spot makes perfect sense. As organizations accelerate their shift into increasingly complex cloud environments, configuration drift, sprawling services, and intricate permission models create far more opportunities for dangerous mistakes. In a world where everything is configurable, misconfigurations become inevitable.
The 2021 “Vulnerable and Outdated Components” being moved into a “Software Supply Chain Failures” category is also logical. Traditional pentests rarely uncover deep supply-chain issues, but across the industry these attacks have become significantly more common and far more damaging. The recent NPM supply chain attack that occurred in September is a perfect example, demonstrating how a single upstream dependency can create massive downstream impact across countless organizations.
Injection and Cryptographic failures categories falling on the list is reasonable, because while these categories have massive CVE volume, OWASP’s methodology measures prevalence per application, not total frequency.
On an encouraging note, the drop in Insecure Design suggests meaningful progress across the industry. More organizations appear to be embracing secure architecture principles early in the development lifecycle. Particularly through practices like threat modeling, secure-by-default patterns, and formal design reviews. While there’s still plenty of room for improvement, the shift hints at a growing maturity in how teams think about security before a single line of code is written.
Meanwhile, Identification and Authentication Failures holding steady reflects that although modern frameworks and managed identity solutions have reduced many common pitfalls, authentication remains a challenge that organizations must continuously get right.
Lastly, the Logging & Alerting Failures category remains at number nine, highlighting a persistent gap in operational security. Many organizations continue to produce logs without the robust alerting, correlation, or response processes needed to detect and contain real threats.
Reflecting on the Brand New Category
OWASP defines the new “Mishanding of Exceptional Conditions” category as the following:
“Mishandling exceptional conditions in software happens when programs fail to prevent, detect, and respond to unusual and unpredictable situations, which leads to crashes, unexpected behavior, and sometimes vulnerabilities.”
While I did not predict that this would become an official top ten category, it does make a lot of sense. Many applications I have tested within the past four years have had some sort of error handling issue, whether that is verbose error messaging containing sensitive information, unchecked error conditions causing unexpected behavior, or other issues.
One of my favorite real-world examples came from a pentest I performed earlier this year where a verbose error message leaked a full local web directory path. This allowed me to easily identify the target web technology, and where the web server was being served from on the local operating system. From that single leak, I was able to identify the underlying web technology and pinpoint exactly where the application was hosted within the operating system. Combined with a file-upload path traversal vulnerability, this insight allowed me to craft and deliver a malicious Java WAR file, ultimately achieving remote code execution on the server.
This is a perfect illustration of how an issue that appears minor in isolation can become a critical vulnerability when chained with others, reinforcing why “Mishandling of Exceptional Conditions” deserves its place on the list.
Conclusion
The newly released OWASP Top 10:2025 certainly brought a few surprises, but upon reflection, the rationale behind the changes is clear. Rising categories like Security Misconfiguration and Software Supply Chain Failures show how modern software environments include complex cloud deployments, sprawling dependencies, and interconnected ecosystems that have shifted the attack surface beyond traditional coding errors. While the steady or falling positions of categories like Injection and Insecure Design highlight that progress is being made in secure coding practices and architecture, even if challenges remain.
What stands out most is OWASP’s continued focus on systemic and operational weaknesses. The categories continue to be more and more broad with a whopping 589 CWEs analyzed to craft this year’s categories.
The OWASP Top 10 continues to serve not only as a benchmark for vulnerability prevalence but also as a guidepost for where the industry should focus next, reminding us that the fight for secure software is always evolving.

About the Author: Jason Marcello
Jason is a Principal Offensive Security Engineer at TCM Security with a deep passion for all things cybersecurity. Jason has professional experience in the healthcare, banking, and tech industries. He specializes in web application security and is especially passionate about research topics pushing the boundaries of application security. Jason holds a Bachelor of Science in Computing Security from Rochester Institute of Technology. Additionally, Jason holds several industry-recognized certifications such as the OSCP, OSWE, OSEP, OSWA, PWPP, BSCP, CRT, CRTO, etc.
Jason is also a husband, dad of two dogs, and a coffee/espresso aficionado. In his free time, he enjoys hiking, gaming, and playing guitar.
Social Media Links:
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcm-sec.com/our-services/
Follow Us: Email List | LinkedIn | YouTube | Twitter | Facebook | Instagram | TikTok
Contact Us: [email protected]
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

