Integrating PCI DSS Auditing and Penetration Testing
Most large businesses, or those that handle payment processing in-house, are subject to the penetration test requirement for PCI DSS compliance. This article will clear up which organizations need penetration tests, what is necessary for compliance, and how consulting with one company for the audit and testing process can streamline compliance and benefit security at a lower cost.
Basics of PCI DSS Compliance
PCI DSS stands for the Payment Card Industry Data Security Standard, a comprehensive set of security requirements for companies that take payment card transactions. The general theme of what PCI DSS asks companies to do can be summed up in one sentence:
Your environment has to be secure if you are processing, storing, or transmitting payment card information.
In practice, this means implementing a range of security mechanisms across your organization’s networks, systems and applications if they have anything to do with payment card information, which we call the Cardholder Data Environment (CDE). Think encryption, access restrictions, penetration testing, and ongoing monitoring.
This leads to struggles and increased costs for many organizations, balancing fragmented service delivery and coordinating between multiple vendors for:
- Vulnerability scanning
- Penetration testing
- Remediation efforts
- Compliance documentation
Thankfully, TCM Security is able to help nearly end-to-end, handling penetration testing, risk consulting and the PCI DSS audit itself under one roof and one contract. But first, let’s take a deeper look at the PCI DSS, as it currently stands.
Understanding the PCI-DSS Landscape
The PCI DSS is currently in v4.0.1, replacing earlier versions of the standard to capture new threats and technologies and bringing in extra requirements with it. One of the first things any organization that knows it needs to get PCI DSS compliant is find out what merchant/service provider level they are, based on their number of card transactions in a given year:
- Level 1: > 6 million transactions per year
- Level 2: 1 – 6 million transactions per year
- Level 3: 20,000 – 1 million transactions per year
- Level 4: < 20,000 transactions per year
Knowing your level lets you know what the requirements are. Level 1 merchants must undergo an annual assessment resulting in a document called a Report on Compliance (RoC) conducted by a certified Qualified Security Assessor (QSA) approved by the PCI SSC – who wrote the standard in the first place. Levels 2, 3, and 4 typically are required to complete a Self-Assessment Questionnaire (SAQ) but can do a full RoC if they choose to.
SAQs range from the fairly simple SAQ-A all the way to the pretty comprehensive SAQ-D, and a full Report on Compliance is a solid undertaking. This is where TCM Security is here to help, able to guide you through what can be an overwhelming process.
The Penetration Testing Requirements Deep Dive
If you’re a business that completely outsources their payment processing and all cardholder data functions to a third party, you’d use a SAQ-A and you wouldn’t need a penetration test, just a vulnerability scan from a PCI DSS Approved Scanning Vendor (ASV) – which we’ll get into later. The same applies if you have terminals (SAQ B), applications (SAQ C) or managed hardware terminals (SAQ P2PE) that don’t store cardholder data.
For everyone else in the SAQ list (and those needing full RoCs), you’re subject to PCI DSS’ requirements for penetration testing. Requirement 11.4 of PCI DSS specifically calls out that
“external and internal penetration testing is regularly performed, and exploitable vulnerabilities and security weaknesses are corrected.”
The standard calls out the following forms of penetration testing as being required to be compliant:
- External penetration testing covering the entire outside perimeter of the CDE, at least annually or after any major architectural change, performed by a qualified third party (11.4.3)
- Internal penetration testing covering inside of the CDE, at least annually or after any major architectural change, performed by a qualified third party (11.4.2)
- If your organization segments off the CDE from the rest of your network (a very common tactic), the effectiveness of these segmentation controls are also required annually or after any major change to these controls (11.4.5)
- Application Penetration Testing apps that link to the CDE or process data is also part of the testing scope of compliance, including threats such as injection flaws, authentication issues, cross-site scripting, and other common web attacks (6.2.4/11.4.1)
TCM Security is able to provide all of these types of testing for our PCI DSS clients – satisfying the independence requirements as a third party, following a PCI-approved penetration testing methodology, and using our extensive PCI experience to correctly scope work efficiently to preserve ever-tighter budgets.
The Integrated Approach Advantage
Penetration testing is just part of getting your organization PCI DSS compliant, though. There’s the small matter of the PCI audit assessment itself, first!
Like we discussed earlier, depending on your merchant level – you’ll be required to complete a SAQ or a full audit resulting in a RoC to get fully PCI compliant for the next year. This process requires thorough documentation of where cardholder data flows through your CDE and where it’s stored. It also requires thorough documentation of things like network architecture, security policies, and control implementation.
It’s all in service of demonstrating that your organization meets all applicable requirements across the 12 domains of PCI DSS. The penetration testing aside, the documentation and evidence-gathering side of PCI compliance represents a significant undertaking on its own.
For most organizations, this means working with an organization that has a PCI-approved Qualified Security Assessor (QSA) on staff. QSAs validate your evidence and ultimately sign off on your PCI compliance in the end. Usually this means two costly vendor evaluations, two contracts to negotiate, two MSAs to sign, but TCM Security stands out for its ability to serve as both penetration testing partner and compliance specialist.
Our QSAs work separately from but closely with our penetration testing team, ensuring that testing results are incorporated seamlessly into your SAQ or RoC documentation. Not only does this result in better remediation guidance, it can drastically reduce the need for redundant meetings and miscommunications between teams.
PCI DSS also requires regular vulnerability scanning of CDE systems from both an internal (11.3.1) and external (11.3.2) perspective, performed quarterly by a PCI Approved Scanning Vendor (ASV). Unlike penetration testing, which involves human testers actively interacting with and attempting to exploit vulnerabilities, ASV scans are primarily automated assessments.
While TCM Security isn’t an ASV, we recognize this as an essential component of your compliance strategy. Fortunately, ASV scanning services are widely available from certified ASVs at relatively modest costs, ranging from a few hundred to a few thousand dollars, depending on network complexity. In practice, TCM Security would work with a trusted ASV partner to ensure this gets folded into a unified delivery solution for you.
Step-by-Step Audit and Pentest Process
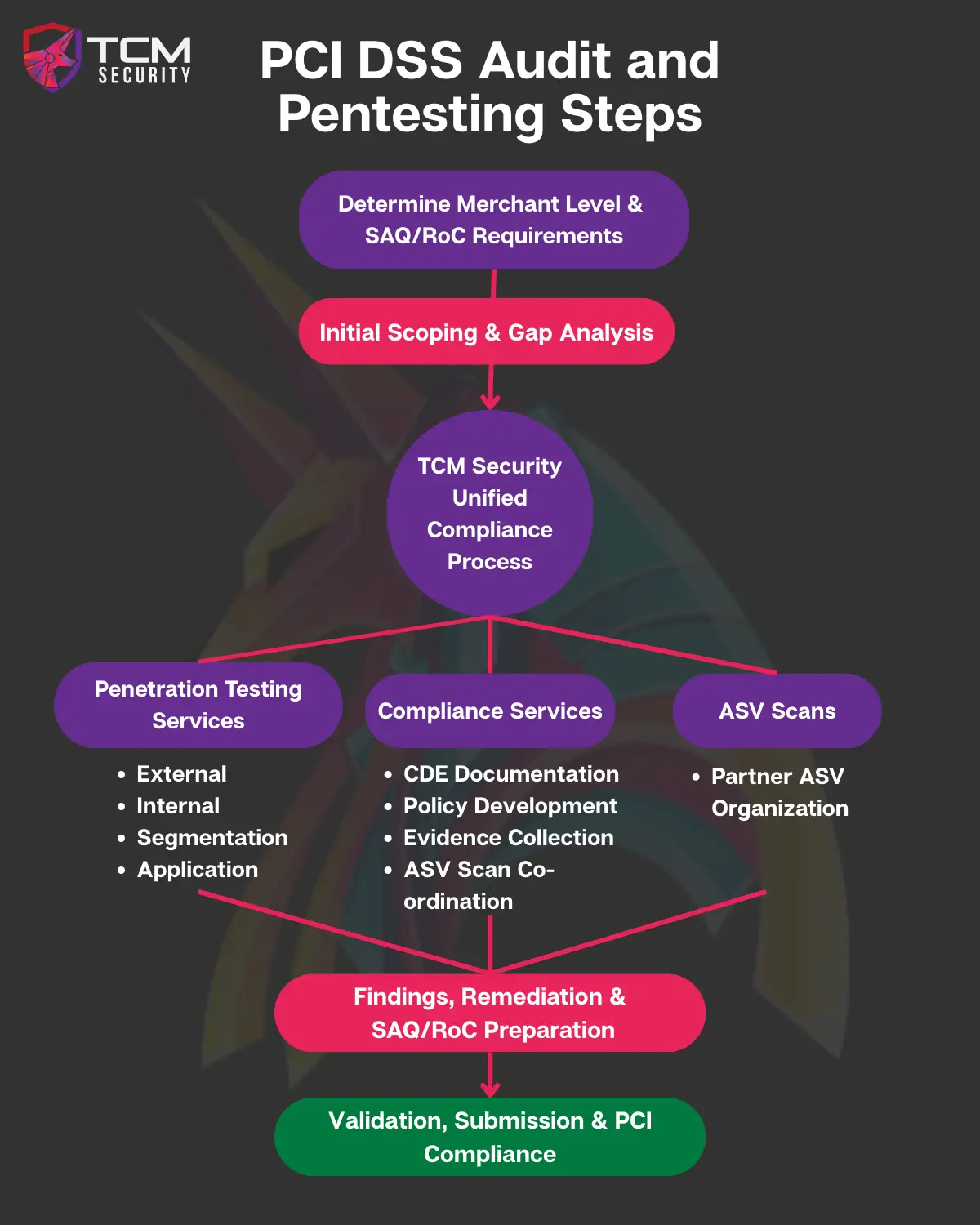
Conclusion
Achieving and maintaining PCI DSS compliance doesn’t necessarily need to be the stressful, difficult process it often is – building a compliant system is meant to be the hard part, remember?
TCM Security is able to offer a unique, integrated approach combining expert penetration testing services, risk consulting and policy support, along with qualified QSAs on staff. We work in tandem with each other and trusted partners (if required) to ensure your organization meets the standards for PCI DSS compliance with the minimum friction possible.
If you are looking for PCI DSS auditing services, especially if you need a penetration test for compliance, contact TCM for a consultation.
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcm-sec.com/our-services/
Follow Us: Email List | LinkedIn | YouTube | Twitter | Facebook | Instagram | TikTok
Contact Us: [email protected]
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

