Code review is an essential part of the web application penetration testing process but is often overlooked. We’re going to look at why it’s important and how to get started.
There are a number of reasons why we might decide to review the source code of an application during the development process, but as penetration testers or ethical hackers, we are doing it to identify vulnerabilities. That’s not to say this is the only goal of code review, it can help to improve code quality, verify controls and ensure a consistent code base. It’s an integral part of any mature development process.
Watch a video version of this article:
Step 1: Understanding Code and the Basic Methodologies
To get started you should have a solid understanding of foundational programming concepts and common languages. If you’re new to the world of programming or returning from a long break then don’t fret – the Internet is flooded with tutorials and courses you can use to acquire skills (including TCM Security Academy’s FREE Programming 100: Fundamentals course). The real trick to getting good is to be consistent and do a bit of coding each day. The languages you need to work with may not entirely be your choice, but since we are dealing with web applications understanding HTML, CSS, and JavaScript is essentially mandatory. Other languages such as PHP, Python, Java and also web frameworks are down to you to decide what’s worth learning.
Following data from input to sink is the first of two methodologies we will discuss. This strategy involves tracing the flow of data from the input source to the point where it is processed, stored, or transmitted by the application. The objective is to identify all the places where the data can be potentially manipulated or abused.
For example, if the application allows user input via a web form, the data flow should be traced to the point where the input is processed or stored, such as a database. Each step along the way should be carefully reviewed to identify potential security weaknesses.
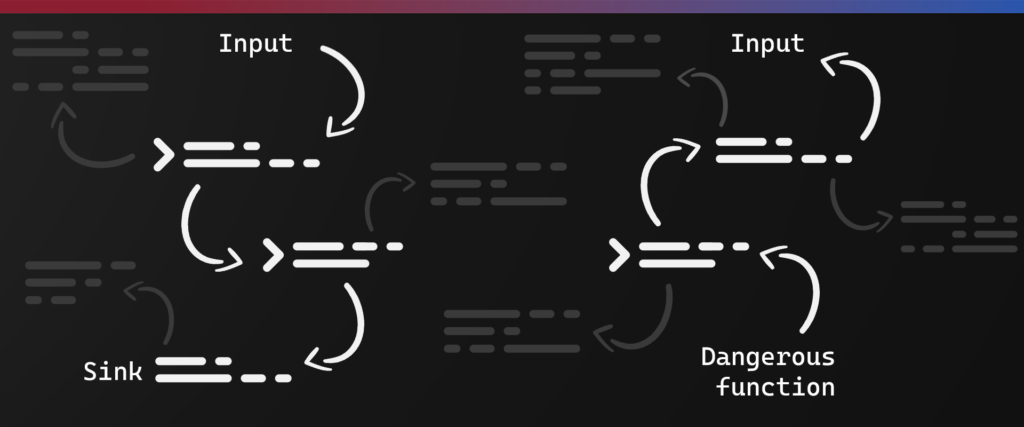
The second strategy is to look for potentially dangerous functions or behavior (such as dynamic SQL queries, or use of the eval() function). Once identified, we can work backwards to understand if there is any parameter or behavior that we control to trigger the dangerous function.
For example, if you did find some dynamic SQL in a web application, and found that a parameter is being placed inside the query, you’d want to verify that the input sanitization or security controls are working effectively. However, even if you’re unable to exploit it at the time, you may still report the finding as a weakness or bad practice.
Step 2: Get Familiar with Automated Tools
SAST (Static Application Security Testing) scanners can help cover a large code base quickly, and identify low-hanging fruit such as hard-coded credentials and the use of dangerous functions. These scanners do have a reputation for giving a high number of false positives but it’s useful still to have them as part of your workflow.
Step 3: Improve your Understanding of Code
This goes beyond just practicing and getting better at writing your own code. Being able to read and understand the code of others is a skill. To improve this skill you can:
-
- Collaborate with developers or attend pair programming
-
- Read documentation
-
- Debug applications live as you review code
Step 4: Practice!
If you’re new to code review, start with small snippets and make sure you get into the habit of keeping documentation. CTFs and other purposely vulnerable applications are a good place to start but I’d recommend moving on as soon as you can to real-world applications. Once you do, don’t measure your success on the number of vulnerabilities found, measure it on how well you understand the application.
Personally, I never do more than 2 hours of code review in one sitting, as my brain tends to wander and skip over things after concentrating on a single thing for that long. Everyone is different so experiment to get the most out of your study or review sessions.

About the Author: Alex Olsen
Alex is a Web Application Security specialist with experience working across multiple sectors, from single-developer applications all the way up to enterprise web apps with tens of millions of users. He enjoys building applications almost as much as breaking them and has spent many years supporting the shift-left movement by teaching developers, infrastructure engineers, architects, and anyone who would listen about cybersecurity. He created many of the web hacking courses in TCM Security Academy, as well as the PWPA and PWPP certifications.
Alex holds a Master’s Degree in Computing, as well as the PNPT, CEH, and OSCP certifications.
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcm-sec.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: [email protected]
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

